Key Takeaways
- Log4j is still present in many applications due to transitive dependencies and outdated libraries, making it a current, not just historical, threat.
- Traditional security tools often bury real threats like Log4j under layers of unrelated alerts, making it hard for developers to know what matters.
- Qwiet helps developers prioritize and fix real vulnerabilities by tracing exploit paths, showing ownership, and cutting through alert noise with precision.
Introduction
The Log4j vulnerability made headlines in 2021, and for good reason; it exposed many systems through a simple, widely used logging library. While most security teams recall the fallout, many developers may assume it has been fully resolved. That’s far from the case. Log4j still exists in thousands of applications, often hidden in indirect or outdated dependencies that receive little attention. In this article, you will learn why Log4j remains a real risk, how it can quietly persist in modern projects, and how Qwiet helps developers surface, verify, and fix it without getting lost in alert fatigue.
Why Log4j Still Matters
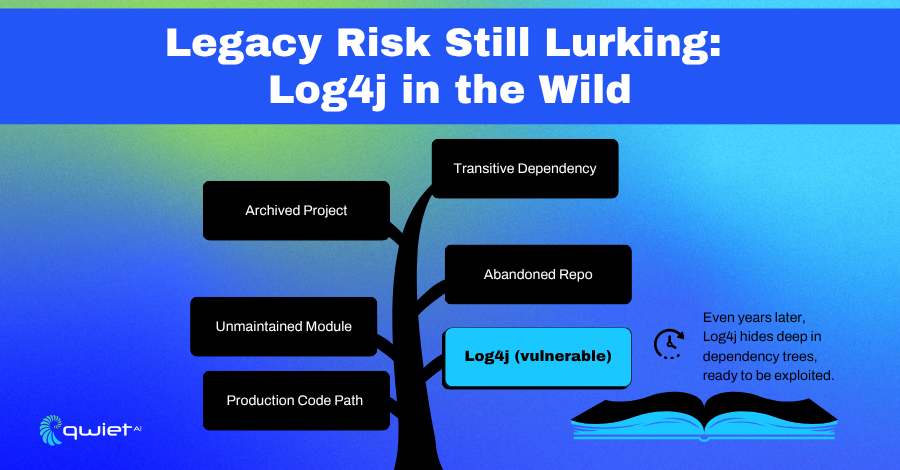
It Didn’t Just Go Away
Log4j didn’t disappear after the headlines. It’s still buried in a massive number of applications, often through transitive dependencies that most devs never touch directly. If a library you import pulls in another that still references a vulnerable Log4j version, your app could still be exposed, even if your codebase never explicitly includes it.
These indirect links are more difficult to identify without a deeper analysis. Package managers don’t always clearly surface the full dependency tree, and if the software hasn’t been updated in a while, something like Log4j can remain hidden in plain sight. This is especially common in microservices or internal tools that were built fast and then left alone.
Fixing Doesn’t Happen Automatically
There’s a general assumption that once a CVE like Log4Shell is publicly disclosed, it will be addressed. But that depends on people knowing it exists in the first place. If the dependency is deep in the stack or part of a third-party package that hasn’t been patched, the risk lingers. Just because a vulnerability is well-documented doesn’t mean it has been resolved across the board.
Millions of apps are still pulling in vulnerable versions of Log4j through outdated or untracked libraries. The scale of the original exposure means even small pockets of vulnerable code can be serious. Without visibility into what’s running in production, it’s easy to miss where the threat still exists, and attackers can easily find it first.
A Developer’s Eye View: Real Example
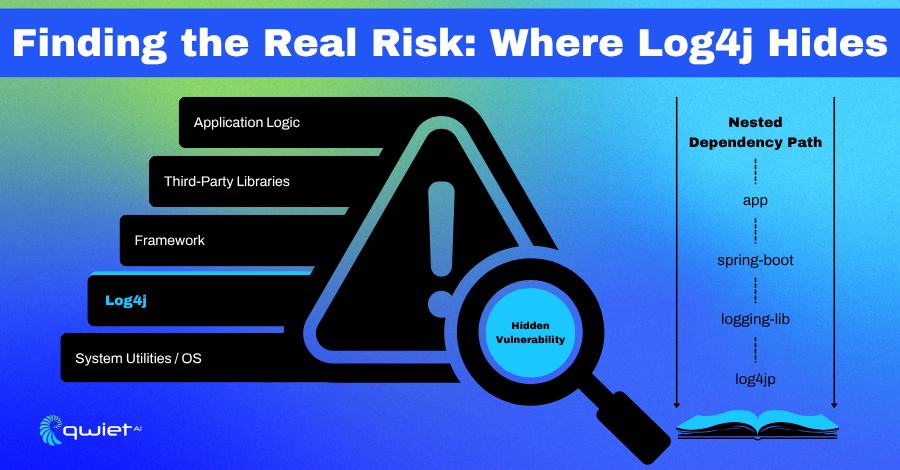
Inheriting Technical Baggage
Imagine picking up a service that has been sitting untouched for over a year. It builds, passes tests, and does what it’s supposed to at least on the surface. There’s no CI coverage for security, no dependency scanning is in place, and the original maintainer is no longer active. Your first instinct might be to leave it alone unless something breaks.
But then you check the dependency tree. You’re not pulling in Log4j directly, but one of the libraries, maybe a logging wrapper or metrics exporter, is. It’s using an older version that includes the vulnerable code. There’s no alert in the repo, no comment in the build file, and unless you’re specifically looking for it, it’s easy to miss.
The scary part is that the runtime behavior still allows for exploitation. It could log user input somewhere deep in the stack. That one edge case, buried in a corner of the app you haven’t touched, could be enough to open the door for remote code execution.
Finding the Signal in the Noise
Here’s the other problem: traditional scanners may technically catch the issue, but they don’t always make it clear where it is or why it matters. You might get dozens of warnings about unused variables, minor linting issues, or low-impact vulnerabilities that distract from what’s dangerous.
In a typical scan report, Log4j might be listed, but without context. There’s no path showing whether it’s reachable, no reference to where in the stack the call occurs, and no insight into whether it even impacts runtime behavior. So it gets treated like another item in the noise pile.
This is where alert fatigue starts. Developers are trained to look for what’s actionable, and when everything is flagged the same way, it becomes hard to know what’s real. Log4j shouldn’t get lost in that mess, but that’s exactly what happens in many pipelines today. Without deeper insight, it’s just another line in a long list of findings.
Alert Fatigue and the False Positive Trap

Too Much Noise, Not Enough Clarity
Most developers have used security tools that dump out massive reports with little to no prioritization. You run a scan and get hundreds of findings, ranging from actual vulnerabilities to irrelevant suggestions that don’t impact runtime behavior. It becomes difficult to discern what requires attention and what’s merely static noise.
Over time, this leads to fatigue. When you can’t tell which issues matter, you stop reacting to alerts at all. They become background clutter, something you scroll past or suppress to get through the build. That’s a problem, especially when a serious vulnerability like Log4j could be buried in the list.
The worst part is when teams spend hours investigating findings that turn out to be false positives or issues that are unreachable in their current deployment context. That time adds up, and it builds skepticism. When a scanner flags something, your first instinct might be to doubt it, even when it’s right.
Context Is What Makes Alerts Useful
Log4j is a perfect example of how alerts can lose their impact without proper context. If a tool flags it but doesn’t indicate whether it’s reachable, how the data flows, or which function it connects to, the default reaction is often to deprioritize it. Developers need more than a CVE ID; they need a clear explanation they can follow.
An alert that shows the full path from input to the vulnerable method changes how developers respond. It’s no longer just a warning; it’s a traceable threat. It becomes something you can test, validate, and fix with confidence. That’s the level of clarity missing from most scan reports.
Without this context, it’s easy to miss real threats or waste time on the wrong ones. Security shouldn’t just point out problems; it should help make decisions. When you know what’s exploitable, what’s reachable, and what’s not, you can act faster and skip the guesswork.
How Qwiet Solves the Problem for Developers
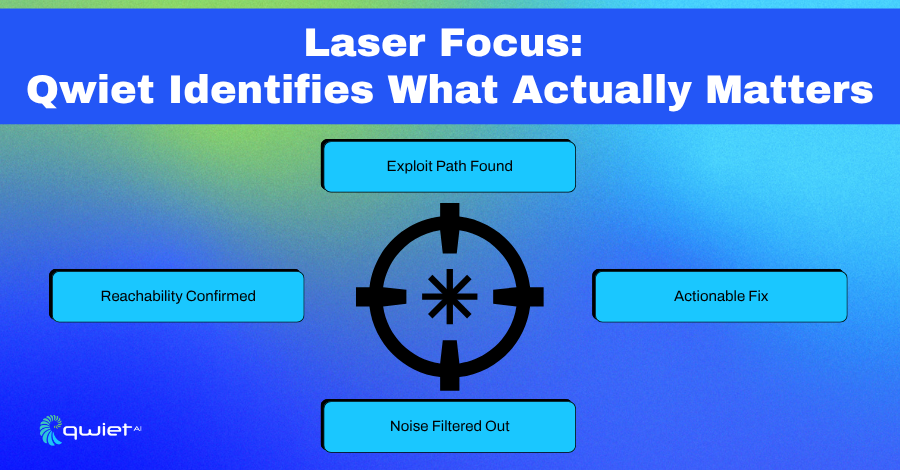
Prioritized Detection That Makes Sense
Qwiet uses a Code Property Graph (CPG) to model how your application works, combining syntax, data flow, and control flow into a unified structure. That’s where the agentic AI layer steps in. It doesn’t just search for known vulnerabilities. It examines actual execution paths, input sources, and the context surrounding each potential exploit to determine what matters.
If Log4j shows up in your codebase, Qwiet doesn’t just flag the version number. It checks whether any reachable paths trigger the vulnerable behavior. You get more than a CVE, you get a trace of how data could move through your application and reach the exploit point. That gives developers a direct way to verify, triage, and take action without second-guessing static findings.
Fix What Matters, Where It Matters
The tool doesn’t stop at detection. It also tells you exactly where the issue lives in the codebase, even if it’s buried under several layers of dependencies. Qwiet ties the finding back to the file, function, or package owner so the right person can address it fast. No hunting through build logs or digging through the dependency tree.
You also get guidance on how to resolve the issue, whether that’s patching a specific library, updating a transitive dependency, or replacing a risky logging call entirely. The goal is to issue fewer generic warnings and provide more direct, developer-friendly fixes. That means less time digging, more time pushing safe code, and better confidence that the work you’re doing reduces risk.
Conclusion
Log4j isn’t just a legacy issue; it serves as a reminder that even well-known vulnerabilities can persist when visibility and context are lacking. Developers don’t need more red flags with no follow-up. They need tools that explain what’s reachable, what’s exploitable, and what needs to be fixed now. With Qwiet, real threats like Log4j don’t get buried; they get resolved, in flow with how developers already work. Book a demo to see how it fits into your environment.
FAQs
Is the Log4j vulnerability still a threat in 2025?
Yes. Despite being disclosed in 2021, Log4j remains present in many systems through indirect dependencies and unpatched code, particularly in legacy or third-party components.
Why do developers still miss Log4j vulnerabilities?
Log4j can be buried deep in transitive dependencies. Without tools that surface reachability and context, many developers don’t realize the risk is still active in their stacks.
How does Qwiet detect and prioritize Log4j vulnerabilities?
Qwiet uses Code Property Graphs and agentic AI to trace whether vulnerable code is reachable and exploitable. It reduces noise by highlighting only real threats.
What makes Log4j difficult to eliminate from codebases fully?
It’s often introduced indirectly through libraries or frameworks. Unless every layer of the dependency tree is scanned and updated, the vulnerability can stay hidden.
How can developers fix Log4j vulnerabilities faster?
Use tools that provide full context, including where the issue resides, who owns it, and whether it’s exploitable. Qwiet streamlines that process directly in the developer workflow.
