Introduction
Within the cascading bytes and bits of digital communications, developers forge pathways of data, threading information through the vast expanse of the internet. However, threats lurking within these pathways seek to intercept, manipulate, and exploit this data. This article ventures into HTTPS and Strict Transport Security (HSTS), offering developers a guide to comprehend, implement, and shield digital interactions from the pernicious reach of MitM attacks.
Introducing HTTPS and HSTS
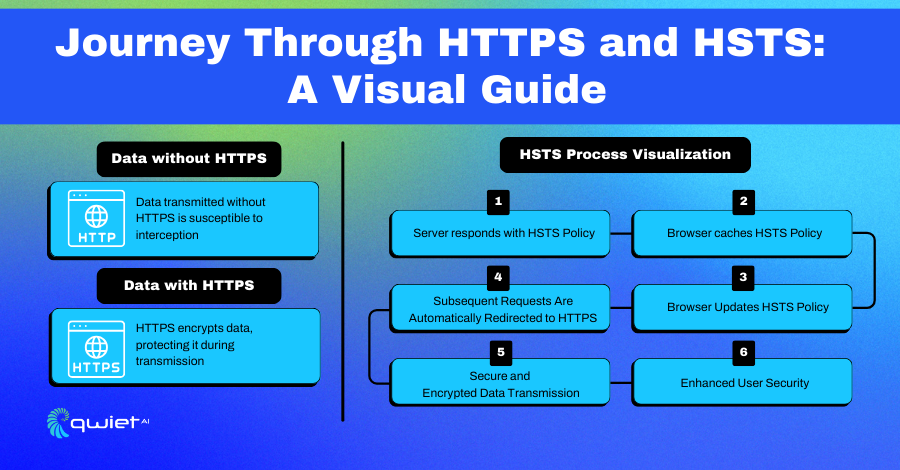
HTTPS, standing for HyperText Transfer Protocol Secure, forms the cornerstone of secure internet communication. It integrates the standard HTTP protocol with an additional layer of encryption, typically provided by SSL/TLS. This encryption is crucial in protecting data from eavesdropping or tampering during its journey across the network.
For developers, HTTPS is not just a protocol but a commitment to user privacy and security. It ensures that all data exchanged between a client and a server is unreadable to any third parties who might intercept it. This is particularly vital in protecting sensitive transactions like online banking, shopping, or any data exchange requiring confidentiality and integrity.
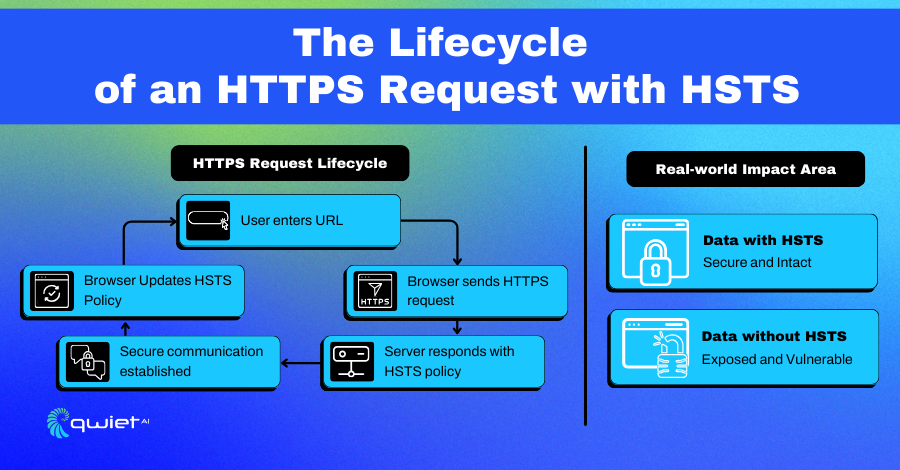
HTTP Strict Transport Security (HSTS) takes security a step further. It is a web security policy mechanism that helps to protect websites against man-in-the-middle (MitM) attacks like protocol downgrade attacks and cookie hijacking.
When a website implements HSTS, it informs the browser only to interact using HTTPS connections. This policy is communicated to the browser through the Strict-Transport-Security HTTP header.
The key benefit for developers using HSTS is the automatic upgrade of all HTTP requests to HTTPS, ensuring secure connections without the risk of a user accidentally accessing the less secure HTTP version of the site.
Implementing HSTS
1. Deciding the max-age:
The max-age directive specifies the duration (in seconds) the browser should remember to access the site only via HTTPS. Choosing an appropriate max-age is crucial: too short, and the security benefits are minimized; too long, and you risk issues if you revert to HTTP. A commonly recommended duration is one year (max-age=31536000).
| Strict-Transport-Security: max-age=31536000 |
2. Embracing All Subdomains with includeSubDomains:
The includeSubDomains directive extends HSTS protection to all subdomains. This is important because it ensures comprehensive security across your entire domain. However, ensure all subdomains support HTTPS before enabling this directive to prevent accessibility issues.
| Strict-Transport-Security: max-age=31536000; includeSubDomains |
3. Enlisting into Preload Lists:
Adding the preload directive and submitting your domain to the HSTS preload list maintained by browsers like Chrome and Firefox ensures HSTS is enforced even before the first visit to your site. This prevents an initial insecure request, but be aware that removing your domain from the list can be lengthy.
| Strict-Transport-Security: max-age=31536000; includeSubDomains; preload |
Challenges in Implementing HSTS
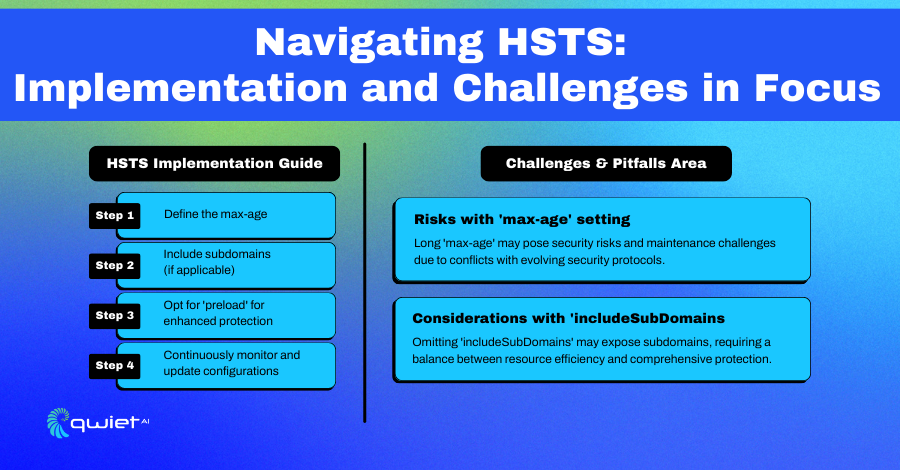
1. The Double-Edged Sword of Prolonged max-age:
While a long max-age benefits security, it comes with significant commitment and risks. If a site’s HTTPS configuration is incorrect or the SSL certificate expires without renewal, users can access the site once the issue is resolved. This can result in substantial downtime and loss of traffic.
To mitigate this risk, developers should:
- Regularly monitor and renew SSL certificates well before expiration.
- Test HTTPS configurations thoroughly in a staging environment before deploying to production.
- Start with a shorter max-age and gradually increase it as confidence in the HTTPS setup grows.
2. Unforeseen Complications with Subdomains:
The includeSubDomains directive ensures that HSTS is applied to all subdomains, but this can be challenging if not all subdomains are prepared for HTTPS. This might include third-party services or legacy subdomains that don’t support secure protocols.
To address these challenges, developers should:
- Work towards upgrading all subdomains to HTTPS, which might involve coordinating with different teams or external vendors.
- Consider implementing HSTS incrementally, starting with primary domains and then progressively including subdomains as they become HTTPS-compliant.
3. Navigating Through Preloading Perils:
Enlisting a domain in HSTS preload lists is a strong commitment. Once a domain is preloaded, it’s difficult to remove and can take months to process. Additionally, every subdomain is affected, and transitioning back to non-HTTPS traffic becomes nearly impossible.
Before opting for preloading, developers should:
- Ensure absolute readiness for HTTPS across all subdomains, as the process is irreversible in the short term.
- Be prepared for the maintenance and monitoring requirements associated with preloading.
- Understand the implications of preloading, including the impact on users and the inability to revert to HTTP without significant challenges.
Strategies to Complement HSTS
1. Content Security Policy (CSP):
Implementing Content Security Policy headers effectively mitigates various types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. CSP allows you to specify which domains the browser should consider as valid sources of executable scripts, thereby preventing the execution of unsafe scripts. A well-configured CSP, in conjunction with HSTS, significantly reduces the attack surface of your web applications.
2. Certificate Pinning:
Certificate Pinning involves specifying the expected certificates or public keys a browser should trust for a particular website. This can prevent MitM attacks that exploit weaknesses in the certificate authority system.
Developers can implement this by pinning the hash of the certificate or public key in the application or through HTTP Public Key Pinning (HPKP), although the latter is being phased out due to its complexity and risks.
Conclusion
While HTTPS lays the foundation for secure data transit, HSTS strengthens this security, ensuring consistent use of HTTPS. Implementing HSTS, however, comes with challenges, such as managing the max-age directive, ensuring HTTPS compliance across subdomains, and navigating the complexities of preload lists. These aspects highlight the need for a detailed, proactive approach to web security. To further strengthen your application’s security posture and navigate these complexities easily, consider scheduling a demo with our team here at Qwiet.