Key Takeaways
- Shift-left alone isn’t enough. With AI-generated code and fast CI/CD, static scans during development can’t detect runtime risk or traceable exploits.
- Shift-everywhere integrates context-aware security. By using tools like Code Property Graphs, ownership mapping, and exploit reachability analysis, teams can embed actionable security logic throughout the SDLC.
- Developers need fewer alerts and more insight. Security should reduce noise, route findings to the right engineer, and block only what’s exploitable without slowing delivery speed.
Introduction
Shift-left practices brought security earlier into the development lifecycle, but they’re no longer meeting the demands of today’s engineering environments. With AI accelerating code generation, CI/CD pushing changes continuously, and code ownership fragmented across teams, static scanning at commit time is insufficient. This article outlines how a shift-everywhere strategy embeds context-aware, developer-aligned security across the full SDLC from coding and build to deploy and runtime, bringing precision and actionability where it’s needed.
Where Shift-Left Hits Its Limits
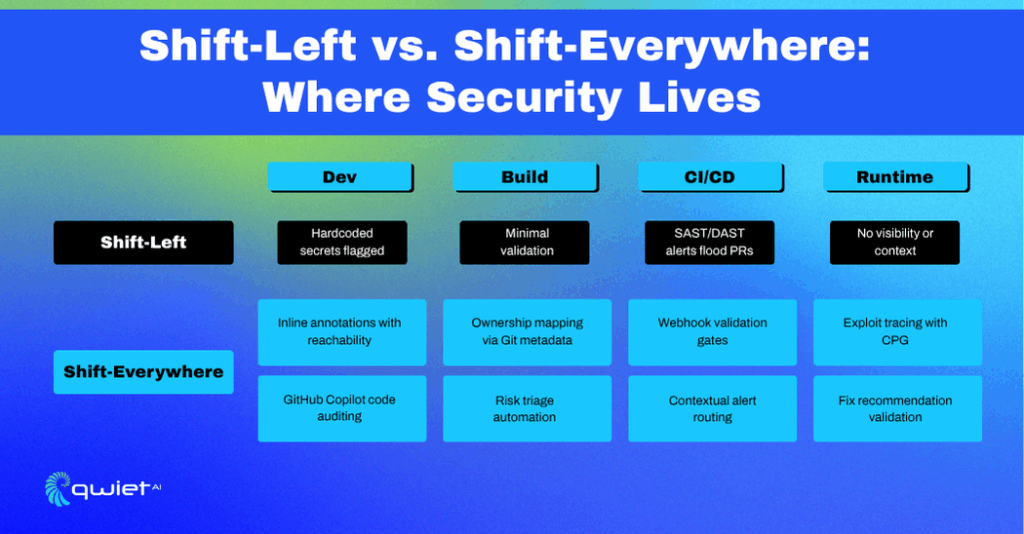
Static Scanning Alone Doesn’t Cut It
Shift-left efforts still depend heavily on running static analysis during early development stages, right when code is committed or reviewed in a PR. While these checks are useful, they don’t offer execution context.
A static engine can flag insecure patterns, but it won’t know if the flagged code is ever actually hit during runtime, whether through input paths, class instantiation, or serialized data flows. This creates a mismatch between what gets flagged and what’s exploitable.
When you’re writing or reviewing code, you need to know whether something is dangerous in context, not just that it could be. Most SAST and IaC tools don’t model how data moves through the system, especially across service boundaries or third-party integrations.
So they’ll throw alerts for patterns that might be unreachable or only trigger under edge-case configurations. This leaves you in the dark about whether it’s worth spending cycles on or if the alert is dead code.
You end up either digging through source and config files to manually confirm reachability, or skipping the alert entirely and hoping it’s low risk. Neither scales, especially when you’re trying to keep your velocity in a CI/CD workflow.
Too Many Alerts, No Signal Path
Security teams often bolt on multiple scanners, SCA, SAST, IaC, and more, with the idea that layered tooling will catch everything. The result is usually the opposite: duplicated findings, conflicting severity ratings, and alerts with no ownership tagging or runtime trace. You’re left parsing raw output with no way to tell who owns what or if any of it matters.
You might get flagged on a vulnerable package buried in a dependency chain five levels deep, one that your service never calls. Or worse, you’ll get five tools flagging the same issue, each with different metadata, none with a clear fix or line of responsibility. That level of noise slows everyone down and creates more backlog than resolution.
After a few cycles of this, teams tune out. Security becomes a background process that you mute unless it blocks a deploy. Not because you don’t care, but because the tools don’t give you the insight to act. Without reachability analysis or ownership context, shift-left security is just static noise in a dynamic system.
Modern Threat Vectors Are Distributed
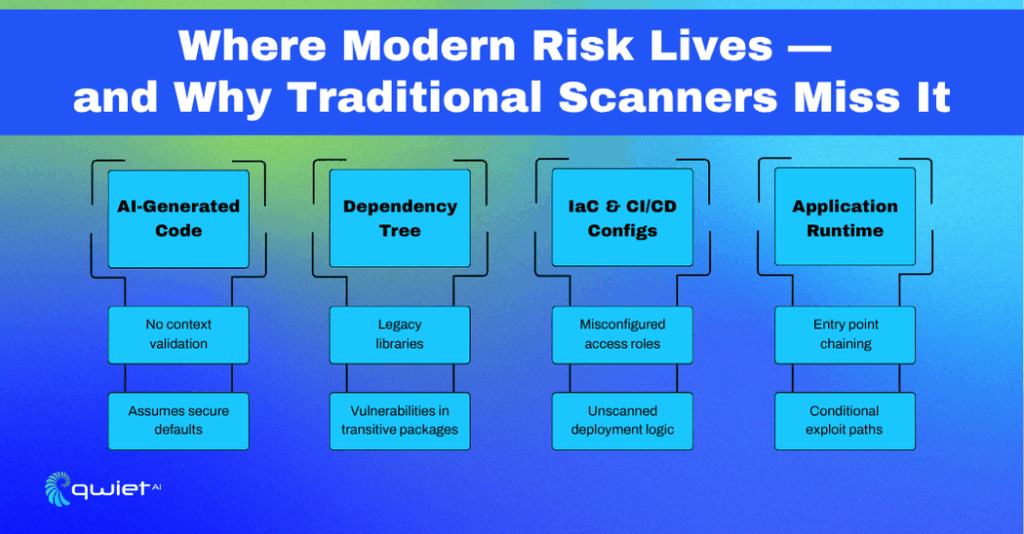
Code Isn’t Written in Isolation Anymore
AI-generated code has changed the development workflow. Tools like Copilot and other code assistants are great for speed, but they often incorporate packages and snippets that haven’t been vetted for security.
You can end up with transitive dependencies that bring in outdated or exploitable libraries, often buried so deep that you’d never spot them without manually digging through the dependency tree.
Security risks don’t stop there; most real-world projects use dozens of open-source libraries and framework plugins, many with their own trees of dependencies. Even if your top-level packages are updated, you might be deploying functions that rely on known vulnerable versions of something buried a few levels down. Static scanners rarely understand this context, so they either miss the issue or dump a huge list of CVEs with no prioritization.
Behavior Over Code: What You Can’t See
Many modern vulnerabilities aren’t in the source code; they’re in how the app behaves at runtime. Think about unsafe deserialization patterns, broken access controls that only manifest with specific input flows, or SSRF routes exposed through obscure API chains. These issues don’t show up in a syntax check or basic lint scan. They require actual data flow tracing or simulated execution to detect.
Static analysis tools are helpful, but they’re stuck at the surface. They don’t analyze runtime state, environment-specific configs, or interaction patterns across services. That’s where real threats hide. If your scanning doesn’t look at how the app is assembled and executed, you’ll miss risks that only show up after the code leaves your IDE.
What Shift-Everywhere Looks Like in Practice

Security That Moves With Your Code
The idea behind shift-everywhere is to track and evaluate security in sync with how software gets built and shipped, not just when code is written. This means integrating logic checks not only in the PR phase but through the build process, deployment automation, and even at runtime. You want your security stack to understand the same system your app runs on, not just the one your linter sees.
To do this well, you need infrastructure that connects the dots. That starts with Code Property Graphs (CPG). They let security tools analyze how data moves through the system, where it flows, how it’s controlled, and where it might reach vulnerable sinks. This makes reachability analysis possible, reducing the number of alerts that aren’t exploitable and highlighting those that are.
Ownership resolution adds another layer of clarity. By tying findings to Git authorship, commit history, or service boundaries, you can route alerts directly to the people who understand the context and can fix the issue. It also helps enforce accountability in shared repos or cross-team services where handoffs get blurry.
Intelligence-Driven Prioritization
Agentic AI pushes this further by adding a reasoning layer. Instead of simply spotting a vulnerable pattern, it evaluates whether that path is reachable, what execution context would trigger it, and whether there’s a real exploit path. It doesn’t just flag the vulnerability; it narrows down to the actionable ones.
When a finding is generated, it’s triaged based on:
- Reachability: Can an attacker-controlled input hit this code?
- Context: Does the execution path align with realistic usage?
- Ownership: Who owns the file or function, and who’s responsible for its lifecycle?
This setup flips the model. Instead of developers digging through 50 static findings to find the one that matters, the system provides them with one that already comes with trace details, a risk assessment, and a clear fix path. That reduces noise and provides teams with a direct path to resolution.
Security logic becomes part of the CI/CD stack itself, not as a monolith but as composable risk gates that can trigger on push, pull request, or deploy. You can plug these gates into GitHub Actions, GitLab runners, or Jenkins pipelines, with conditions like “only block merges if reachable vulnerabilities are found in modified files.” That means fewer blanket blocks, more relevant feedback, and much faster time to fix.
Developer Workflows Without Security Drag
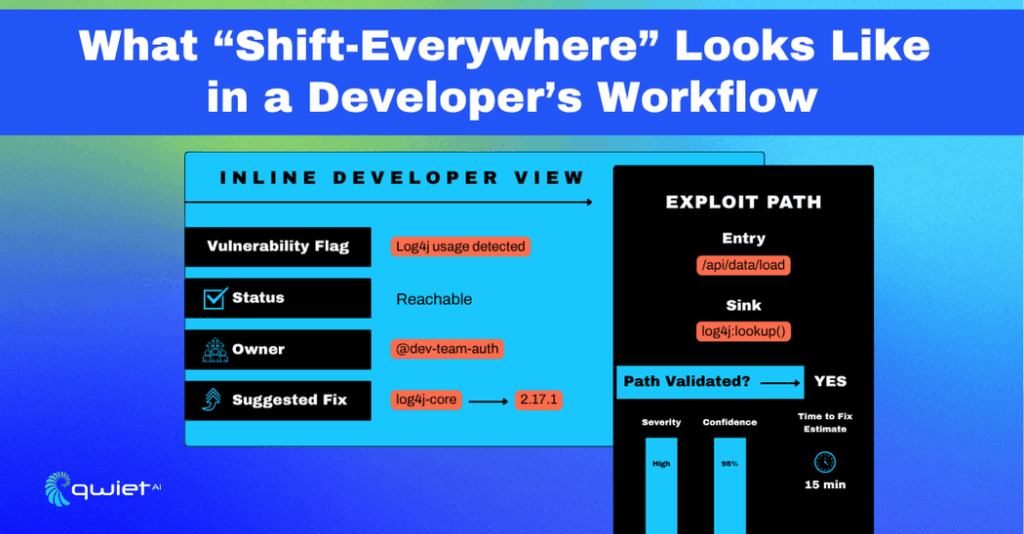
Security Feedback That Respects Your Workflow
As a developer, the fastest way to address a security issue is when it appears in the context of your existing work. That’s why inline pull request annotations matter; they’re not just about calling out a vulnerability, they deliver the reasoning behind it. You’ll see the exploit path, the affected function, and why it matters for your branch: no context switching, no hunting for documentation, no guesswork.
What makes this effective is the validation that underlies it. These aren’t theoretical matches based on pattern recognition; they’re real findings, linked to actual data and control flow from your code. If it’s reachable, it shows up. If it’s not, it doesn’t get in your way. That precision lets you focus on risks that impact what you’re building today, not old CVEs that haven’t been exploitable for months.
Alerts with Context, Routed to the Right Engineer
Security alerts tend to get ignored when they lack clarity or end up in the wrong place. That’s why routing matters. With Git history, ownership tags, and branch-level metadata, findings can be sent to the engineer who owns the relevant service or wrote the affected function. You’re not wading through team inboxes or stale Jira tickets; you’re getting a direct message that connects the issue to your code.
Slack and ChatOps integrations make this even smoother. Updates can be scoped to active branches or filtered to match specific release tags, ensuring that the alerts you see are always relevant to your current work.
You’re not buried in noise from other teams or unrelated repos. And because every alert includes reachability analysis and runtime exposure, there’s no need for back-and-forth validation. You know it’s real. You know it’s yours. And you can move on it with confidence.
Conclusion
Shifting everywhere isn’t about layering on more tooling; it’s about wiring security logic into the same workflows developers already use. By aligning findings with real code paths, execution context, and code ownership, teams get fewer false flags and faster fixes. DevSecOps must keep pace with modern development, which is characterized by modularity, observability, and speed. Want to see how that can work in your org? Book a demo with Qwiet AI and see it live in your pipeline.
FAQs
What is shift-left security, and why is it limited today?
Shift-left security refers to practices that push security checks earlier in the software development lifecycle. It’s limited because it often relies on static scans that lack execution context, leading to false positives and developer fatigue.
What does “shift security everywhere” mean in DevSecOps?
It means embedding context-rich, actionable security insights at every phase of development, from code to build, deploy, and runtime, so alerts are relevant, reachable, and routed to the right engineer.
How does Qwiet AI help with modern DevSecOps?
Qwiet utilizes Code Property Graphs and agentic AI to trace actual exploit paths, map findings to code owners, and eliminate unreachable alerts, providing developers with only what matters.
Why do developers ignore security alerts?
Developers often dismiss alerts when they lack clarity, contain unreachable risks, or don’t indicate actual exploitability. Without context, alerts become noise instead of insight.
What are the benefits of reachability analysis in security tools?
Reachability analysis determines whether a vulnerability can be exploited from a real entry point. This helps teams prioritize risks and focus on the code paths that matter most.
