Introduction
Did you know that a simple website visit could put your personal information at risk? In this article, we explain how a common online threat called XSS can cause big problems and show you ways to keep your application secure.
What is Cross-Site Scripting (XSS)?
Cross-site scripting (XSS) is a significant web security vulnerability that enables attackers to inject malicious scripts into content that other users see. This type of attack exploits a user’s trust in a particular site, allowing the attacker to send malicious code to an unsuspecting user through the web application.
Unlike other web attacks, XSS does not directly target the web application itself; instead, it targets the web application’s users, making it uniquely dangerous and widespread.
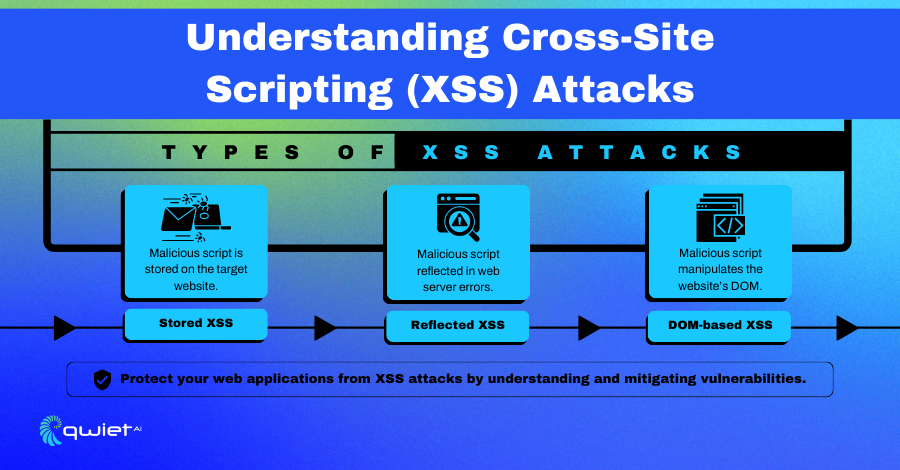
There are three primary types of XSS attacks:
Stored XSS (Persistent XSS)
This occurs when a malicious script is permanently stored on the target server, such as in a database, message forum, visitor log, comment field, etc. The malicious script is executed every time a user accesses the stored data.
Example 1: Stored XSS
| <!– A comment form on a blog post –> <form action=“/submit_comment” method=“POST”> <textarea name=“comment”></textarea> <button type=“submit”>Submit Comment</button> </form> |
In a Stored XSS attack, an attacker might submit a comment that includes a malicious script like <script>alert(‘XSS’);</script>. Suppose the website properly sanitizes the input before displaying it to other users. In that case, the script will execute in the context of the user’s browser, potentially leading to session hijacking, data theft, or other malicious outcomes.
Reflected XSS (Non-Persistent XSS)
This happens when a malicious script is reflected off a web application to the user’s browser. It is typically delivered via email or another external link and tricks the user into submitting a request to a web application, which includes the attack in the response.
Example 2: Reflected XSS
| <!– A search form –> <form action=“/search” method=“GET”> <input type=“text” name=“query”> <button type=“submit”>Search</button> </form> |
For a Reflected XSS attack, the attacker could craft a URL that includes a malicious script in the search query, such as /search?query=<script>alert(‘XSS’);</script>. If the search results page reflects the user’s query without sanitization, the script will execute, leading to the same potential risks as Stored XSS.
DOM-based XSS
In this scenario, the vulnerability exists in the client-side code rather than the server-side code. The attack occurs when the web application’s client-side script writes user-provided data to the Document Object Model (DOM) without proper sanitization. The attacker manipulates the DOM environment in the victim’s browser, which executes the malicious script.
Example 3: DOM-based XSS
| // JavaScript that takes the URL fragment and writes it to the page document.getElementById(‘someElement’).innerHTML = window.location.hash.substr(1); |
In a DOM-based XSS attack, an attacker could manipulate the URL to include a malicious script, which then gets written and executed by the DOM. For instance, navigating to http://example.com/page#<script>alert(‘XSS’);</script> would execute the script when the page uses the URL fragment without proper sanitization, exploiting the DOM-based XSS vulnerability.
XSS attacks can have severe consequences for both users and organizations. They can steal user data, such as cookies and other session information, allowing attackers to hijack user sessions.
How does an XSS work?
XSS attacks revolve around the injection and execution of malicious scripts in a victim’s browser, exploiting vulnerabilities in web applications that fail to sanitize user inputs properly. Understanding XSS attacks’ core components and processes is crucial for developers and security professionals to defend against these insidious threats effectively.
Mechanisms of XSS Attacks
The fundamental mechanism of an XSS attack involves injecting malicious scripts into web content viewed by other users. These scripts are executed by the victim’s browser as if they were part of the legitimate content of the webpage, enabling the attacker to execute a wide range of malicious activities. The execution context provided by the victim’s browser gives XSS its potency; the malicious script runs with the same privileges as content originating from the website, allowing it to access cookies, session tokens, and other sensitive information.
Role of User Input in XSS Vulnerabilities
User input plays a critical role in XSS vulnerabilities. Web applications often accept user input—such as form data, URL parameters, and cookies—and then display it as part of the web page. Suppose an application does not properly sanitize this input.
In that case, an attacker can include malicious scripts in their input, which the application will then unwittingly execute within the browsers of other users. The failure to appropriately encode or sanitize user inputs is the primary vector through which XSS attacks are launched.
Process from the Attacker’s Perspective
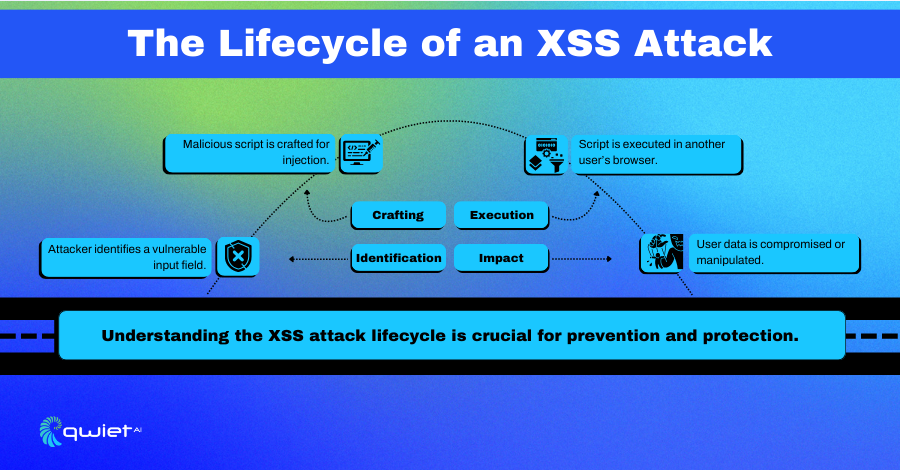
From the perspective of an attacker, executing an XSS attack involves several steps:
- Finding a Vulnerable Input: The first step is to identify a point of injection, which is a component of the web application that accepts user input and reflects it back to the user without adequate sanitization. This can involve thorough testing of all input vectors, including form fields, URL parameters, and HTTP headers.
- Crafting a Malicious Script: Once a potential injection point has been identified, the attacker crafts a script designed to exploit the vulnerability. The nature of the script can vary widely, from simple alerts (used to demonstrate the presence of a vulnerability) to complex payloads designed to steal cookies, session tokens, or perform actions on behalf of the victim.
- Executing the Attack: With the malicious script ready, the attacker then needs to deliver it to the victim. This can be done through various means, such as embedding the script in a URL that the victim is tricked into clicking (reflected XSS), posting it to a public forum where it is stored and displayed to other users (stored XSS), or manipulating the DOM of a webpage the victim visits (DOM-based XSS).
Throughout this process, the attacker exploits the inherent trust between the client (victim’s browser) and the server (web application), using the web application as a vector to deliver malicious scripts to users.
XSS Migitation Best Practices
To effectively shield web applications from Cross-Site Scripting (XSS) attacks, adopting and rigorously applying a set of best practices that address the underlying vulnerabilities these attacks exploit is essential. The following are core strategies to prevent XSS:
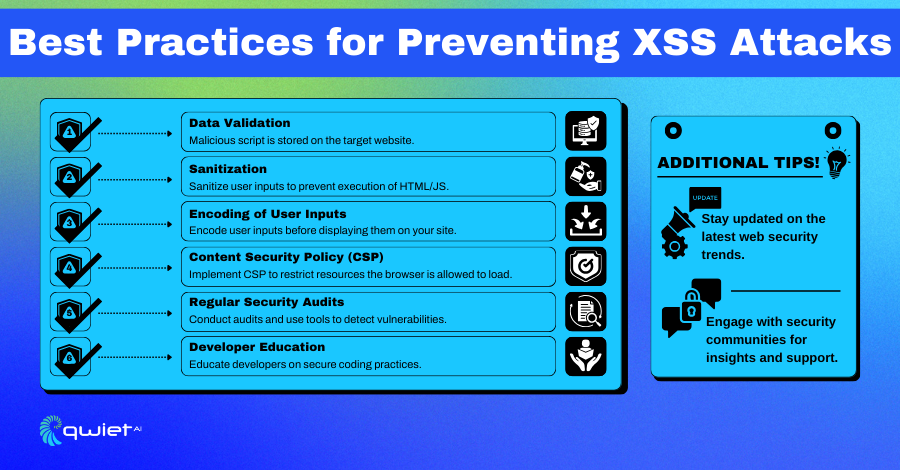
Data Validation
Data validation involves verifying input against a set of rules before accepting it. By validating input data, applications can prevent malicious scripts from being stored on the target website. This could include checking for data types, lengths, formats, and ranges. Robust data validation is the first line of defense against XSS.
Sanitization
Sanitizing user input is crucial for preventing the execution of malicious HTML or JavaScript code. Sanitization includes stripping out unwanted data such as scripts or SQL code, ensuring that only clean, safe input is accepted. This means actively removing or neutralizing any potentially malicious code within user inputs before they are used within output.
Encoding of User Inputs
Encoding involves converting user input into a safe format treated as data, not executable code. By encoding user inputs before they are displayed on the site, you ensure that even if an input contains code, the browser will not render it as code but instead display it as data.
Content Security Policy (CSP)
Implementing a Content Security Policy (CSP) is a powerful tool for reducing the severity of XSS attacks. CSP is a browser feature that helps detect and mitigate certain types of attacks, including XSS and data injection attacks. It allows you to specify which dynamic resources are allowed to load, thereby preventing the loading of unauthorized or malicious scripts.
Regular Security Audits
Regular security audits are vital for identifying and addressing new vulnerabilities that could be exploited for XSS. Use tools like Qwiet, specifically designed to detect XSS vulnerabilities by scanning your codebase for potential injection points.
Developer Education
Finally, educating developers on secure coding practices is indispensable. Developer awareness on topics such as how XSS attacks work, the latest web security trends, and how to code defensively can drastically reduce the likelihood of vulnerabilities being introduced into code.
Conclusion
We’ve discussed XSS and how to prevent it from affecting you, including tips like checking inputs and setting up good security rules. Remember, knowing about these dangers is the best way to avoid them. If you need help or want to learn more about protecting your codebase against XSS attacks, contact our team at Qwiet to book a demo.