Introduction
SQL Injection poses a formidable threat to the integrity of data-driven applications. In this blog post, we dive into the nuances of SQL Injection, from its operational mechanisms and various attack vectors to the vulnerabilities it exploits. Readers will gain essential knowledge and practical strategies to fortify their applications against this pervasive threat, ensuring a robust cybersecurity defense with valuable techniques and code examples.
What is SQL Injection?
SQL Injection is a security vulnerability that undermines the integrity of database-driven applications. This attack targets the interaction between user input fields and the database layer. Attackers exploit vulnerabilities in the application’s data processing methods to insert or “inject” malicious SQL commands into input fields, such as login forms or search boxes.
This technical manipulation is far from simple; it requires a deep understanding of SQL syntax and the application’s database structure. The consequences of successful SQL Injection attacks are severe, leading to unauthorized disclosure, modification, or destruction of sensitive data. This could range from accessing private user credentials to manipulating or exfiltrating confidential financial records, posing a significant risk to data integrity and privacy.
How does an SQL Injection Attack work?
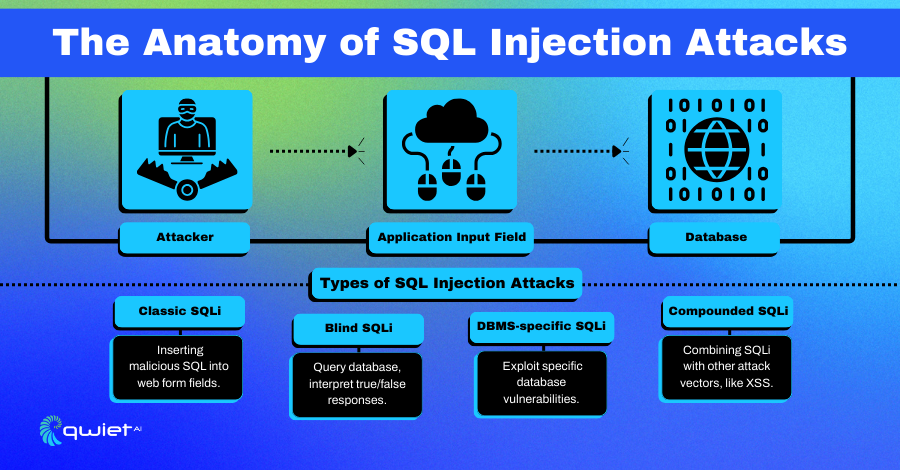
SQL Injection attacks can come in various forms, each with its own method of exploitation and impact, some common types include:
- Classic SQLi: The most straightforward form of SQL Injection, where the attacker directly inserts malicious SQL into a query via input fields, leading to immediate execution.
- Blind or Inference SQLi: More covert and complex, this technique doesn’t directly reveal data. Instead, attackers send payloads that inquire about the database by observing the application’s responses to specific queries, allowing them to infer the data within.
- Database Management System-specific SQLi: These attacks exploit vulnerabilities specific to particular database management systems, leveraging their unique syntax and features for unauthorized access or data manipulation.
- Compounded SQLi: This form combines SQL Injection with other attack vectors, such as Cross-Site Scripting (XSS) or Denial of Service (DoS), to magnify the impact or bypass security measures that would otherwise stop a straightforward SQLi attack.
Now that we know what types there are, let’s dive into understanding SQL Injection. By breaking down the process into actual code snippets, we can focus more clearly on how it’s executed, which will help us recognize the threat and implement preventive measures.
In a typical scenario, a user is prompted to enter their username and password, which the application checks against its database to grant access. The SQL query used for this might look like:
| SELECT * FROM users WHERE username = ‘user_input’ AND password = ‘user_password’; |
Here, user_input and user_password are placeholders for the actual input from the user.
An attacker wants to log in without a valid password; they exploit the input field by entering a specially crafted username and manipulating the SQL query.
For the username, the attacker inputs admin’ —, and for the password, anything or nothing.
The input admin’ — is designed to end the query prematurely and comment out the rest of the SQL command. The SQL command sent to the database looks like this:
| SELECT * FROM users WHERE username = ‘admin’ –‘ AND password = ‘whatever’; |
In this manipulated query, everything after the — is considered a comment and ignored by the SQL database. The query effectively becomes:
| SELECT * FROM users WHERE username = ‘admin’; |
This query searches for a user named ‘admin’ without checking the password, granting the attacker unauthorized access if such a user exists.
Looking at these simple steps and code examples helps us understand how SQL Injection works. It highlights why it’s important to check and clean the data users enter to keep our systems safe from such attacks.
SQL Injection Mitigation Best Practices
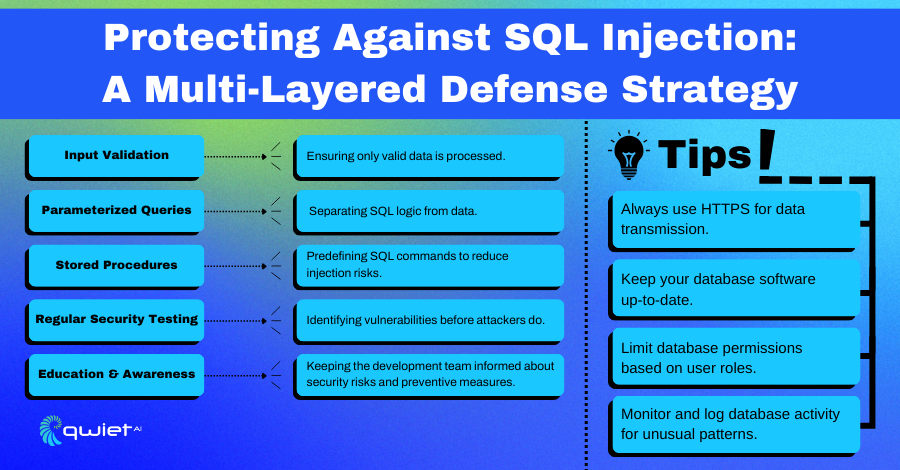
Adhering to best practices in security and coding is imperative to fortify applications against SQL injection. These measures not only help prevent unauthorized access but also ensure the integrity and confidentiality of the data. By implementing these best practices, organizations can significantly mitigate the risk of SQL Injection attacks.
Input Validation
Input validation involves verifying that only properly formatted data is entered by users. By enforcing strict input validation, applications can reject suspicious or malicious data that doesn’t conform to expected patterns.
For example, an email input field should only accept data that matches the structure of an email address. This can be achieved through regular expressions or custom validation logic.
| # Example of email input validation in Python import re def is_valid_email(email): pattern = r”^[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}$” return re.match(pattern, email) is not None # Usage email = “[email protected]” if is_valid_email(email): print(“Email is valid.”) else: print(“Invalid email format.”) |
This Python code snippet demonstrates how to validate an email address using regular expressions (regex). The function is_valid_email checks if the provided email matches a specific pattern that represents a standard email format: it starts with letters, numbers, or certain symbols, followed by an ‘@’ sign, then the domain name with a period, and ends with a 2 to 4 letter domain suffix.
If the email fits this pattern, the function confirms its validity. The usage example tests an email address and prints out whether it’s valid based on this validation process.
Parameterized Queries
Parameterized queries, also known as prepared statements, are a powerful defense mechanism that ensures the database treats input data as parameters rather than executable code. This approach effectively separates SQL code from data, mitigating the risk of SQL Injection.
SQL example with parameterized queries:
| — SQL using parameterized queries SELECT * FROM users WHERE username = ? AND password = ? |
In many programming languages, this concept is implemented using placeholders for data in the SQL statement, which are then filled with the actual input values by the database driver or ORM.
| # Example of parameterized query in Python using SQLite import sqlite3 conn = sqlite3.connect(‘example.db’) cursor = conn.cursor() # Parameterized query username = ‘user’ password = ‘password123’ cursor.execute(“SELECT * FROM users WHERE username=? AND password=?”, (username, password)) |
The Python code snippet above demonstrates using a parameterized query with SQLite to access a database securely. Using the sqlite3 library, it first establishes a connection to a database named ‘example.db’. It then prepares a cursor object to execute SQL commands.
The code safely queries the ‘users’ table in the parameterized query section, looking for a record matching a specified username and password. The placeholders ? in the SQL command are filled with username and password variable values, preventing SQL injection by separating the query structure from the data values. This method ensures that user input is handled securely, reducing the risk of malicious injections.
Use of Stored Procedures
Stored procedures can encapsulate SQL logic on the database side, reducing the exposure to SQL Injection by limiting direct access to the database structure. The attack surface is minimized by predefining SQL commands and granting applications only permission to call these procedures.
| — Example of a stored procedure in SQL Server CREATE PROCEDURE GetUserByUserName @username VARCHAR(255) AS BEGIN SELECT * FROM users WHERE username = @username END |
This SQL Server code snippet shows how to create a stored procedure named GetUserByUserName. This procedure takes one parameter, @username, which is a text string up to 255 characters long. Inside the procedure, it runs a command to find and return all information from the ‘users’ table for the user with the matching username. This approach encapsulates the query inside a reusable procedure, enhancing security and efficiency.
Regular Security Testing
Keeping your software safe requires regular security checks, which are vital for finding and fixing vulnerabilities. Automated tools, like Static Application Security Testing (SAST), play a key role here. They sift through your code automatically, spotting common security flaws without slowing development. This allows for quick identification and patching of vulnerabilities, making your software more secure.
Conclusion
In our discussion about preventing SQL Injection, we’ve covered key steps such as checking inputs, using safe queries, and the need for ongoing security checks. These aren’t just suggestions; they’re essential for protecting your data from online threats. Qwiet can help take preventative measures to protect your app against common SQL attacks; book a demo today to learn more.