What is DevSecOps?
DevSecOps stands for Development, Security, and Operations. It’s an approach that builds security into every part of the software development process. Instead of adding security measures at the end, DevSecOps makes security a key part of the workflow from the very beginning. This method encourages development, operations, and security teams to work together to deliver secure software quickly and efficiently.
DevOps combines software development (Dev) and IT operations (Ops) to speed up software delivery through better teamwork and continuous delivery. However, as cyber threats became more advanced and regulations stricter, it became clear that security needed to be integrated into the DevOps pipeline from the start. Traditional methods of adding security at the end were needed for the fast-paced world of modern software development.
This need for better security led to the creation of DevSecOps. In DevSecOps, security is embedded throughout the entire DevOps lifecycle, not just at the end. This shift means taking proactive steps and monitoring continuously to keep software secure. DevSecOps helps create more secure applications and enables faster, safer releases by using automated security tools early in the development process.
Principles of DevSecOps
Shift-left Security
Shift-left security means bringing security into the software development process as early as possible. Instead of waiting until the end to check for security issues, developers start thinking about security from the beginning, during the design and coding stages. This early focus helps catch and fix vulnerabilities right away, making the whole project more secure and less expensive to fix later on.
Automation and Continuous Integration
Automation and continuous integration are key to making DevSecOps work smoothly. By using automated security tools like SAST and DAST within continuous integration (CI) pipelines, teams can constantly check for vulnerabilities as new code is added. This real-time feedback helps quickly identify and fix security issues, keeping the development process efficient. Automation ensures that security checks are consistent and thorough without slowing the workflow.
Collaboration Between Development, Security, and Operations Teams
For DevSecOps to succeed, development, security, and operations teams must work closely together. This collaboration ensures that everyone shares responsibility for security. Regular communication and joint efforts, like threat modeling and risk assessments, help prioritize security throughout the development process.
Benefits of DevSecOps
DevSecOps brings many advantages by making security a part of every step in the software development process. These benefits improve security, ensure compliance, and speed up software delivery.
Early Detection and Remediation of Security Issues
DevSecOps helps find and fix security problems early by building security checks into the development process. Using tools like SAST and DAST, teams can spot potential threats as soon as they arise. This proactive approach means problems are addressed before they become major issues, reducing the risk of security breaches and keeping projects on track.
Improved Compliance and Reduced Risk
By integrating security into every stage, DevSecOps ensures that software meets industry standards and regulations. Automated security checks and continuous monitoring help identify and fix compliance issues quickly, reducing the risk of fines and legal problems and providing a secure and reliable software environment.
Faster Time-to-Market with Secure Software
DevSecOps speeds up secure software delivery by automating security testing and integrating it into development. This reduces manual work and delays, allowing for quicker release cycles. As a result, the software can be delivered to market faster, meeting business needs and staying competitive while maintaining high-security standards.
DevSecOps Practices and Strategies
Certain practices and strategies are key to making DevSecOps work. These practices ensure continuous and effective security throughout the software development process.
Integrating Security into CI/CD Pipelines
Adding security checks into Continuous Integration and Continuous Deployment (CI/CD) pipelines is crucial. This means security tests are done at every stage, from code writing to deployment. This way, any security issues can be found and fixed immediately, preventing insecure code from going live.
Automated Security Testing (SAST, DAST, IAST)
Automated security tests are a major part of DevSecOps. Tools like SAST, DAST, and IAST help with this. SAST checks the source code for problems, DAST tests the application while running, and IAST combines both. Automating these tests helps catch security issues early and fix them quickly.
Secure Coding Practices and Code Reviews
Secure coding practices and regular code reviews are essential. Developers need to follow secure coding guidelines to avoid introducing vulnerabilities. Code reviews by security experts help find and fix any security issues early. This ensures that every piece of code is as secure as possible.
Threat Modeling and Risk Assessment
Threat modeling and risk assessment are important strategies. Threat modeling identifies possible security threats during the design phase. Risk assessment examines how likely these threats are and how severe they could be. This helps prioritize which security issues to address first.
Continuous Monitoring and Feedback Loops
Continuous monitoring and feedback are vital for ongoing security. Monitoring tools track the application’s performance and security in real-time, alerting teams to any issues. Feedback loops provide insights to improve security practices over time. This constant monitoring ensures that security is always up to date.
Tools and Technologies for DevSecOps
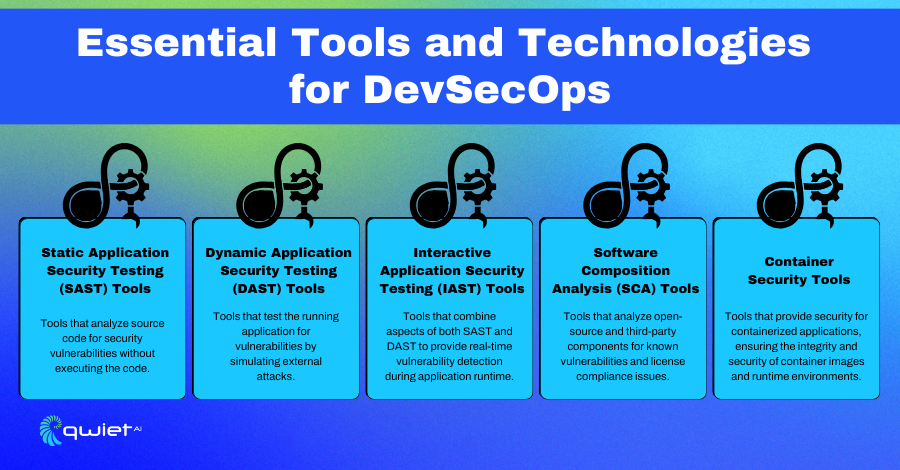
Static Application Security Testing (SAST) Tools
Static Application Security Testing (SAST) tools analyze source code for vulnerabilities without running the program. This early detection allows developers to fix issues before deploying the software, ensuring a secure codebase.
Dynamic Application Security Testing (DAST) Tools
DAST tools test applications in their running state to find security weaknesses that could be exploited. These tools don’t require access to the source code, making them useful for evaluating application security in real-time. They help identify issues such as SQL injection and cross-site scripting.
Interactive Application Security Testing (IAST) Tools
IAST tools blend the capabilities of SAST and DAST by examining code in real time during execution. This provides a detailed understanding of how vulnerabilities manifest when the application runs, offering a comprehensive view of potential security risks.
Software Composition Analysis (SCA) Tools
SCA tools manage and secure third-party components and open-source libraries used in applications. By identifying known vulnerabilities in these dependencies, SCA tools guide mitigating risks. This ensures that all software parts, including external components, are secure.
Container Security Tools
Securing containerized environments like Docker and Kubernetes is crucial, and container security tools are designed for this purpose. They offer vulnerability scanning, compliance checks, and runtime protection, securing containers from creation through deployment and during operation. These tools help maintain a secure and resilient container infrastructure.
Conclusion
DevSecOps adds security to every development step, helping development, security, and operations teams work together. This approach finds issues early, ensures compliance, reduces risk, and speeds up delivery with CI/CD integration, automated testing, secure coding, and continuous monitoring. Using DevSecOps is key to building secure applications.
Improve your DevSecOps with Qwiet to catch vulnerabilities early. Book a demo to see how it can enhance your security posture.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
