What is Dynamic Application Security Testing (DAST)?
Dynamic Application Security Testing (DAST) is a security testing approach that focuses on identifying vulnerabilities in a live application. Instead of analyzing the code, DAST interacts with the running application, mimicking an attacker’s actions to uncover security flaws.
DAST sends inputs and requests to the application while running and observes how it responds. This method allows DAST to detect issues like SQL injection, cross-site scripting (XSS), and other vulnerabilities found only when the application operates.
Why is DAST Essential?
DAST is important because it finds vulnerabilities that only appear when the application is live. By interacting with the application in real time, DAST can identify issues related to input handling, authentication, and session management that might not be visible through static code analysis.
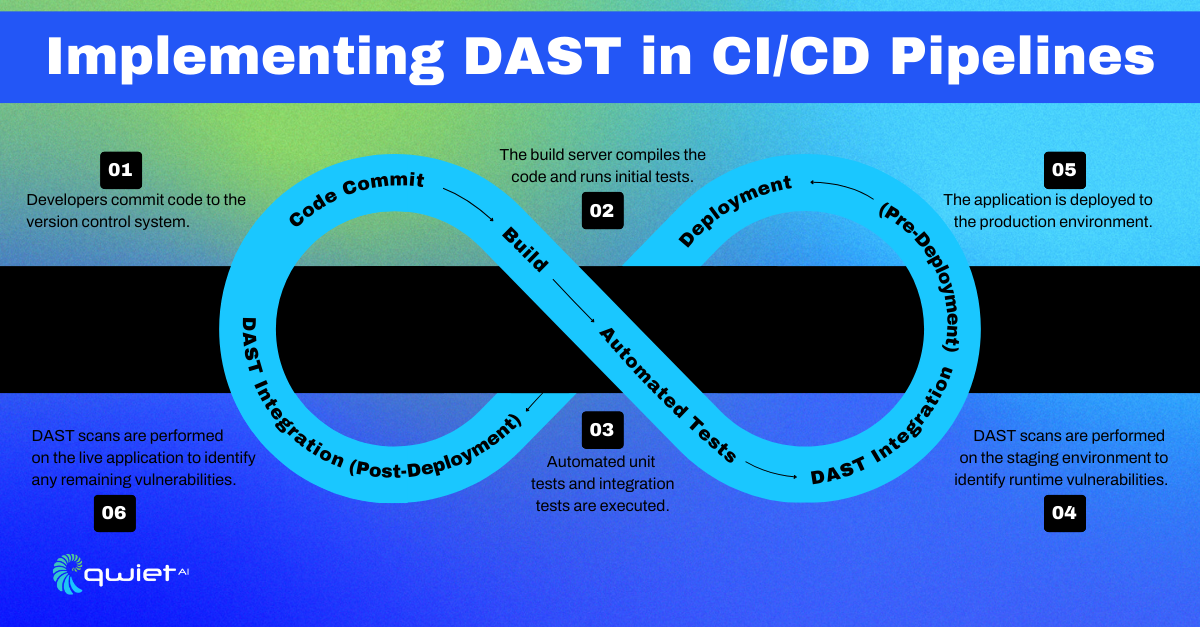
DAST is valuable in continuous security integration, especially within DevOps pipelines. Integrating DAST into your CI/CD process allows regular security testing throughout development and deployment, catching vulnerabilities before they reach production.
Types of DAST Tools
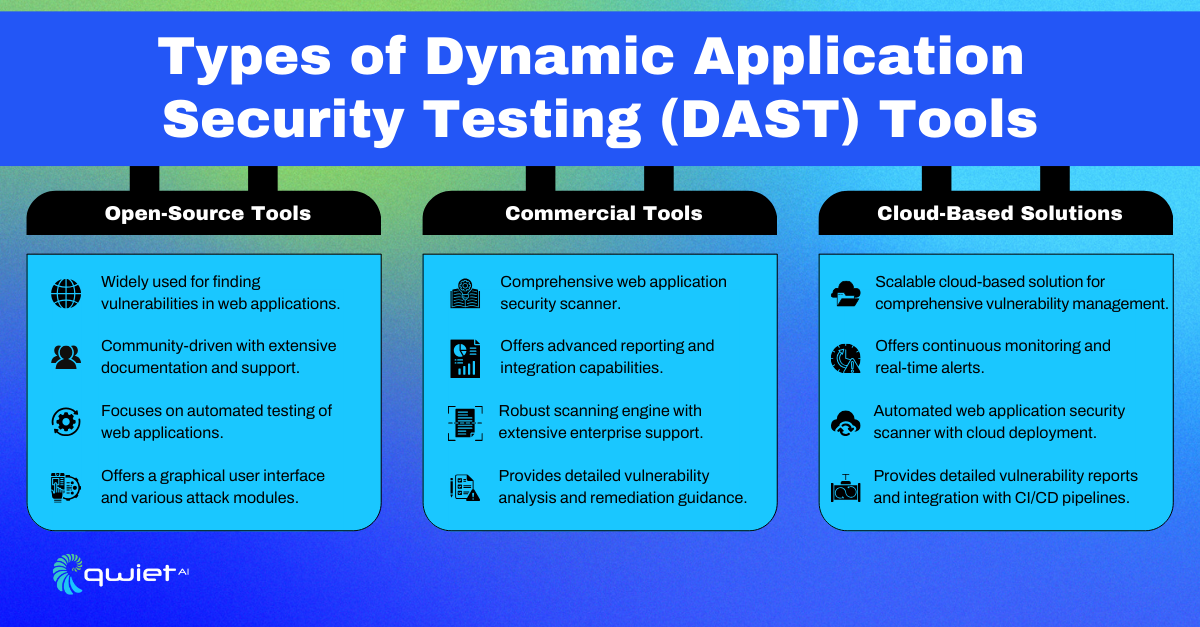
Open-Source Tools
Open-source DAST tools are freely available options for testing application security. These popular tools offer a range of features to help identify application vulnerabilities.
The main advantage of open-source DAST tools is that they’re free and highly customizable, making them accessible for developers with limited budgets. However, they may require more manual setup and might not offer the same support or advanced features as commercial options. Additionally, updates and new features might be less frequent than paid solutions.
Commercial Tools
Commercial DAST tools are paid solutions that often come with more advanced features and dedicated support. Compared to open-source alternatives, commercial DAST tools typically offer more user-friendly interfaces, better automation, and more in-depth analysis. They also often include customer support and regular updates, making them a more reliable option for organizations that need consistent performance and advanced features without extensive manual configuration.
Cloud-Based DAST Solutions
Cloud-based DAST tools offer the benefits of scalability and ease of use. They can be accessed from anywhere without needing to install software locally. These solutions can easily scale with your organization’s needs, and they often come with automated updates and maintenance handled by the provider, reducing the burden on your team.
Components of DAST
Scanning and Crawling
DAST tools scan and crawl through your application like a user or a bot would. They explore the structure, forms, and inputs to find potential entry points where an attack could happen. This helps map out the entire application to identify areas that might be vulnerable.
A thorough scan is important because it ensures every part of your application is checked for vulnerabilities. The more complete the scan, the better your chances of catching hidden issues that attackers might exploit. It’s about covering all the bases to ensure no potential threat is overlooked.
Attack Simulation
DAST tools simulate attacks by injecting malicious inputs into various application parts, like forms or URLs. These tools act like an attackers, trying to exploit weaknesses such as poor input validation to see how the application handles it.
DAST tools test the most common attack vectors, including SQL injection, where harmful SQL commands are executed, and cross-site scripting (XSS), where malicious scripts are injected into web pages. They also test for weak spots like insecure authentication and direct object references, covering many potential threats.
Vulnerability Analysis
Once DAST tools detect a vulnerability, they analyze how the application responds to the simulated attack. This helps to understand where the problem lies and what could happen if the vulnerability isn’t fixed.
After analysis, vulnerabilities are categorized by severity and their potential impact on your application. This helps prioritize which issues must be fixed first so that you can focus on the most pressing threats.
Reporting
DAST tools provide detailed reports on all the vulnerabilities they’ve found, including specifics on what was detected and where it was located. These reports often include actionable recommendations on how to fix the issues, making it easier for developers to address them.
These reports can also be integrated with other security tools and dashboards, helping to create a more streamlined security process. This integration allows teams to track vulnerabilities alongside other security efforts, making managing and resolving issues easier.
Conclusion
DAST plays a vital role in modern application security by identifying vulnerabilities that only appear during runtime. Integrating DAST into your security strategy helps protect your applications from potential threats. Make DAST a core component of your security efforts, and explore how Qwiet can enhance your approach. Start strengthening your application security today—book a demo with Qwiet.
Read Next
SBOM Compliance Simplified: What U.S. Companies Need to Know
Introduction A Software Bill of Materials (SBOM) is like a detailed list of all your software’s components, licenses, and dependencies. It helps you see exactly what’s in your software and manage potential risks more effectively. As cybersecurity threats grow and regulations tighten in the U.S., SBOM compliance is becoming a top priority. From government mandates […]
Swift and Secure Networking in iOS Apps
Introduction Networking in iOS apps is key for fetching data and real-time updates, but it also brings security risks. This post covers the basics of networking in iOS, focusing on URLSession and Alamofire for efficient network communication, and highlights best practices for securing these interactions. You’ll learn how to build robust and secure networking in […]
Threat Modeling
What is Threat Modeling? Threat modeling is a way to find and fix potential security problems in a system. We can understand how attackers might take advantage of these issues by looking at how the system is built and spotting weak points. This helps us get a clear view of the system’s security and identify […]