What is Incident Response?
Incident Response (IR) is a structured process for identifying, managing, and addressing security incidents such as cyberattacks, data breaches, and other threats. It helps organizations respond quickly and efficiently to minimize damage, limit the attack’s spread, and restore normal operations.
The main goals of Incident Response are to reduce the impact of security incidents, minimize recovery time and associated costs, and preserve any evidence needed for potential legal or forensic investigations. A well-defined IR plan ensures a swift, coordinated response to threats.
Incident Response (IR) focuses on handling security incidents like cyberattacks. At the same time, Disaster Recovery (DR) is broader, covering all aspects of business continuity after any major disruption, including natural disasters or system failures. IR addresses immediate security threats, whereas DR involves restoring the business to full operation.
Importance of Incident Response in Cybersecurity
Mitigating the Impact of Security Incidents
A well-structured Incident Response plan equips organizations to quickly identify and contain security threats such as malware, ransomware, or data breaches. With predefined detection, investigation, and containment protocols, response teams can isolate the threat before it spreads to other systems or causes further damage. This approach minimizes the impact on operations and prevents the attacker from gaining a stronger foothold in the network.
Reducing Recovery Time and Costs
An effective Incident Response plan streamlines the recovery process by outlining clear steps for eradicating the threat and restoring affected systems. With rapid detection and containment, organizations can reduce downtime, data loss, and the cost of remediation. With the right tools and processes, response teams can swiftly bring operations back online, limiting financial losses and preventing prolonged disruptions.
Maintaining Trust and Compliance
Incident Response helps mitigate threats and plays a crucial role in maintaining trust with customers and partners. Organizations that take a structured approach to handling security incidents are prepared to protect sensitive data.
In addition, a well-managed Incident Response plan ensures that organizations meet compliance standards for reporting breaches and safeguarding data, reducing the risk of legal penalties or regulatory sanctions.
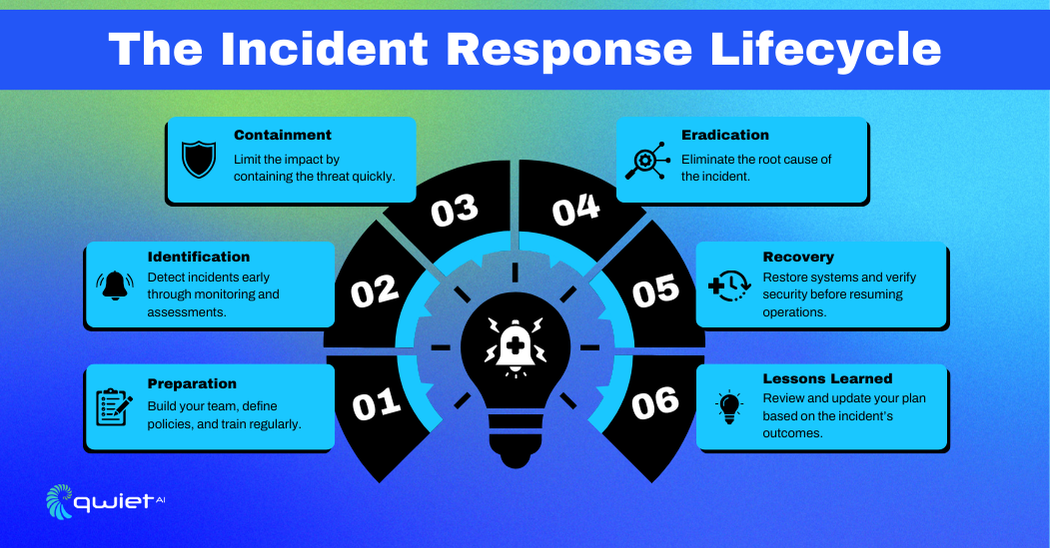
Key Components of an Incident Response Plan
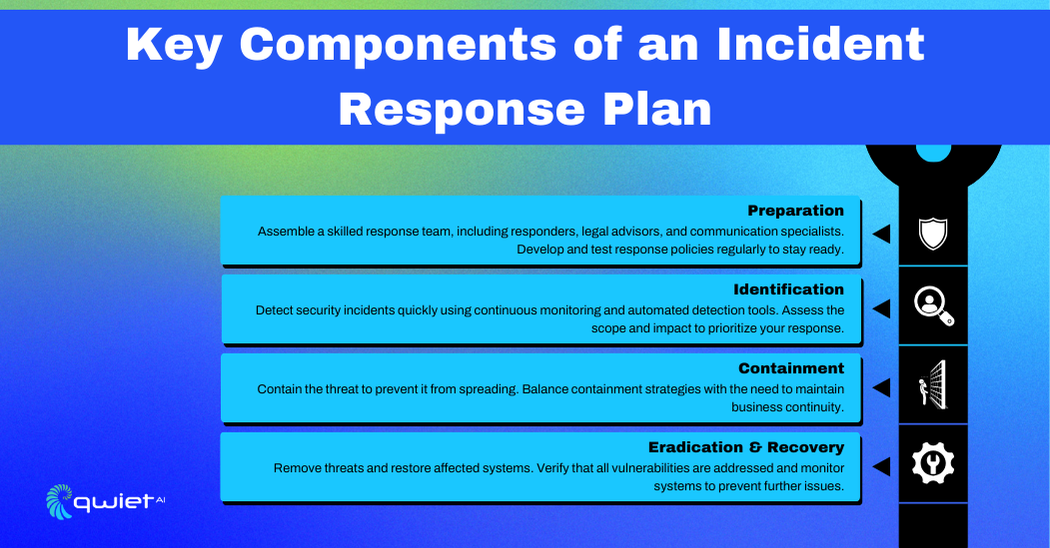
Preparation
Building a Strong Incident Response Team
A successful Incident Response (IR) plan starts with assembling a skilled and well-rounded team. This includes security experts who can detect and respond to incidents, legal advisors who can manage regulatory and legal concerns, and communication specialists who can handle internal and external messaging during an incident. Each role is critical in coordinating an efficient response, ensuring all aspects of the incident are covered.
Developing and Testing Incident Response Policies
Creating clear Incident Response policies is only part of the preparation. Equally important is regularly testing these policies through drills and simulations.
These tests allow the IR team to validate their response strategies, identify gaps, and ensure that all team members understand their roles during real incidents. Continuous testing helps keep the organization prepared for a variety of scenarios.
Identification
Detecting Security Incidents Quickly
Early detection is key to limiting the damage from a security incident. Continuous monitoring systems, such as Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools, play a critical role in detecting threats in real-time. These automated systems provide immediate alerts, helping the IR team to act before the incident escalates.
Assessing the Scope and Impact of Incidents
Once an incident is detected, the IR team must quickly assess its scope and potential impact. This assessment involves identifying which systems and data have been compromised and determining the severity of the incident. The findings guide the response strategy, allowing the team to prioritize actions based on the most critical areas affected.
Containment
Short-Term vs. Long-Term Containment Strategies
Short-term containment focuses on isolating the immediate threat to prevent it from spreading further, such as disconnecting compromised devices from the network.
Long-term containment strategies involve addressing the incident’s root cause, ensuring that vulnerabilities are patched, and hardening systems to prevent the attacker from regaining access.
Balancing Containment with Business Continuity
While containing a threat, the IR team must also consider the need to keep business operations running smoothly. This balance requires strategic decisions about which systems can be isolated without causing major disruptions, allowing the organization to mitigate the threat while minimizing the impact on day-to-day functions.
Eradication and Recovery
Removing Threats and Restoring Systems
After containing the threat, the next step is to remove the incident’s root cause, such as deleting malware or closing exploited vulnerabilities. Once the threat has been eliminated, systems are securely restored from backups, ensuring no malicious code remains that could reignite the attack.
Validating and Monitoring Systems Post-Recovery
Even after systems are restored, ongoing monitoring is essential to confirm that the threat has been entirely eradicated. The IR team continuously checks for any lingering issues, such as residual malware or attempts to re-compromise the system, ensuring the environment remains secure.
Lessons Learned
Conducting Post-Incident Analysis
After handling an incident, conducting a post-incident analysis helps the IR team evaluate their response. This review identifies what worked well, what went wrong, and areas that can be improved. Organizations can refine their strategies by analyzing each incident and enhancing their ability to respond to future threats.
Updating Incident Response Plans Based on Lessons Learned
The insights from post-incident analysis should be used to update and improve the IR plan. This could involve refining detection methods, adjusting containment strategies, or reworking communication protocols. Regular updates based on real-world incidents strengthen the organization’s overall security posture and preparedness for future events.
Types of Incident Response Models
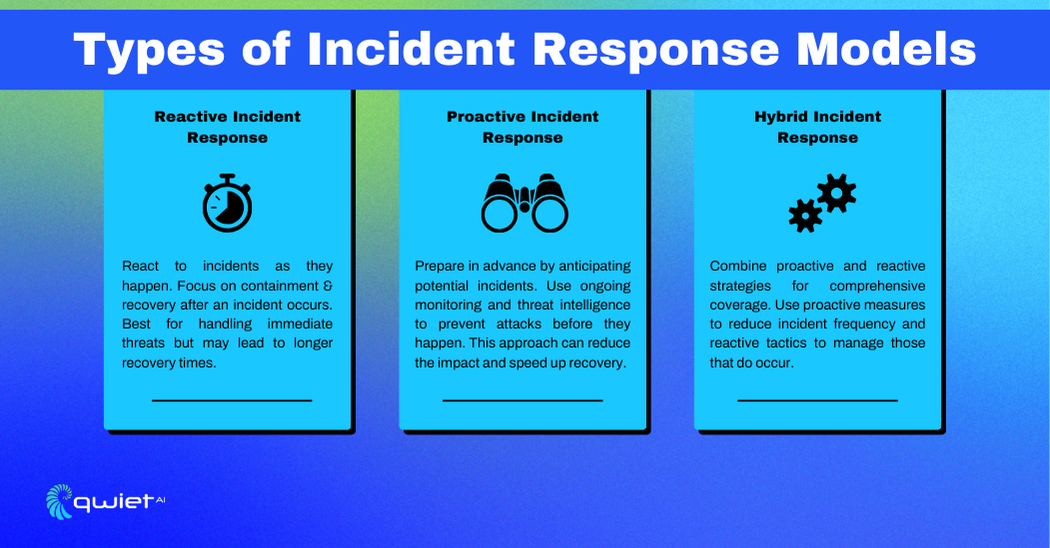
Reactive Incident Response
Reactive Incident Response focuses on addressing security incidents only after they have been detected. The primary objective is to contain the threat and recover compromised systems. This approach relies on well-defined procedures for isolating the affected areas and initiating recovery efforts, minimizing the spread and impact of the incident once it’s already underway.
While reactive IR is effective in containment and recovery, it tends to have longer response times, leading to more severe damage. Without early detection mechanisms, organizations may struggle to contain incidents quickly, resulting in extended downtime and higher recovery costs. Additionally, threats that go unnoticed for longer periods can lead to a deeper compromise of systems and data.
Proactive Incident Response
Proactive Incident Response emphasizes ongoing preparation and monitoring to detect and neutralize threats before they escalate. It involves continuous network monitoring, gathering threat intelligence, and conducting regular drills or simulations to keep the IR team ready.
Being proactive offers several advantages, including faster detection of security events and quicker response times. This early intervention reduces the overall impact of incidents, allowing organizations to contain threats before they cause significant damage.
Hybrid Incident Response
A hybrid approach merges the benefits of proactive and reactive strategies. By integrating continuous monitoring and preparation with strong recovery protocols, organizations can quickly detect and respond to incidents while having solid plans in place for containment and recovery. This model offers a more adaptable framework, responding to incidents both in real-time and post-event.
Conclusion
Incident Response (IR) is a critical process for managing security incidents quickly and minimizing damage. It involves preparation, early detection, containment, recovery, and post-incident analysis to improve future responses. By having a well-structured IR plan, organizations can reduce the impact of security threats, lower recovery costs, and maintain customer trust. To improve your Incident Response and application security, book a demo with Qwiet today and explore how our solutions can help.
Read Next
Microservices Security Overview
What is Microservices Security? Microservices security is the comprehensive approach to safeguarding each service within a microservices architecture. In this model, each service functions independently, which creates unique security requirements for each one. To secure these distributed services, microservices security involves methods to protect inter-service communications, secure APIs, and manage access and identity across multiple […]
Salt Typhoon’s Impact: Could AI-Powered AppSec Have...
Key Takeaways AI Could Have Altered the Salt Typhoon Attack: AI-driven solutions, such as real-time anomaly detection and proactive vulnerability identification, would have identified and blocked threats before they escalated. Supply Chain Visibility is Essential: AI-enhanced SBOMs continuously monitor third-party components, highlighting outdated or vulnerable dependencies that attackers, like Salt Typhoon, exploit. Integrated Security Strengthens […]
Penetration Testing (Pentesting) Overview
What is Penetration Testing? Penetration Testing, or pen testing, is a security practice where experts try to break into your system, network, or application to find weaknesses. This controlled attack helps organizations see where they are vulnerable and fix those issues before real hackers can exploit them. The main goal of penetration testing is to […]