Key Takeaways
- Live Security Assurance: Real-time SBOM (Software Bill of Materials) verification ensures that software dependencies remain secure and compliant throughout the development lifecycle.
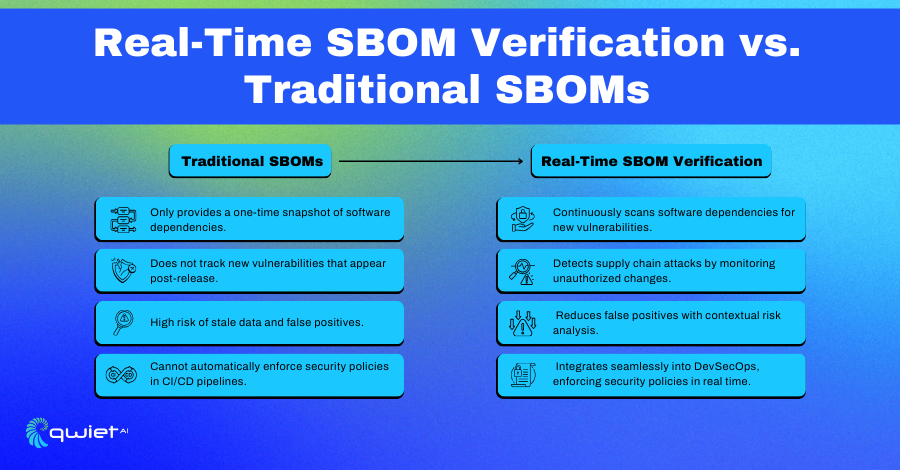
- Beyond Static SBOMs: Traditional SBOMs provide a snapshot in time, but real-time verification continuously monitors for new vulnerabilities and risks.
- Automated and Scalable: Integrating real-time verification into DevSecOps workflows enhances security without slowing development.
What is Real-Time SBOM Verification?
Real-time SBOM verification continuously monitors and validates software dependencies to detect emerging vulnerabilities, license issues, and security threats. Unlike static SBOMs, which generate a one-time snapshot of components, real-time verification keeps track of changes and updates as they happen. This approach provides an ongoing assessment of dependencies’ security and compliance status, allowing teams to detect and respond to risks in near real time.
Traditional SBOMs have significant limitations because they only capture a fixed list of dependencies at a specific time. They don’t account for newly discovered vulnerabilities that arise after the initial SBOM is created. Real-time verification addresses this gap by offering continuous risk management. By actively checking dependencies against live vulnerability databases and security policies, it helps organizations proactively mitigate risks before they impact production environments, ensuring that applications remain secure throughout their lifecycle.
Why Does Real-Time SBOM Verification Matter?
Security
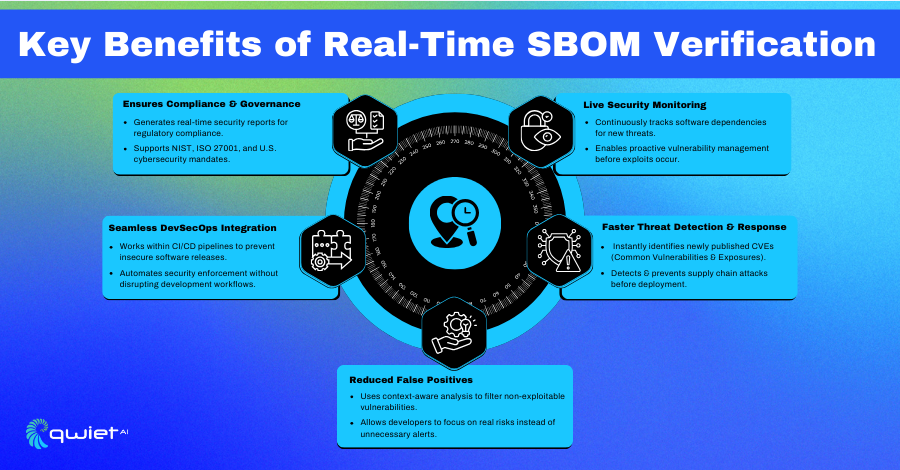
Real-time SBOM verification allows security teams to detect new vulnerabilities as soon as they are published, addressing Common Vulnerabilities and Exposures (CVEs) before they can be exploited. It continuously monitors for unauthorized or compromised components in the software supply chain, reducing the risk of supply chain attacks. Tracking updates and patches for dependencies in real-time helps maintain an accurate and up-to-date risk assessment, ensuring that potential threats are caught early.
Operational Benefits
One major advantage of real-time verification is that it reduces false positives. Traditional tools often flag outdated or irrelevant vulnerabilities, wasting time and resources. Real-time verification focuses on actionable insights, helping teams concentrate on real risks. It integrates seamlessly into DevSecOps workflows, working within CI/CD pipelines without slowing development. This also improves supply chain visibility, allowing teams to track and manage third-party dependencies more effectively.
Compliance and Governance
Real-time verification helps organizations meet security standards like NIST, ISO 27001, and emerging SBOM-related regulations, including the U.S. Executive Order on Cybersecurity. It provides audit-ready reports that simplify compliance documentation and support security assessments. This also extends to license compliance, identifying potential risks related to open-source licensing violations and giving teams a clear picture of their compliance status.
Components of Real-Time SBOM Verification
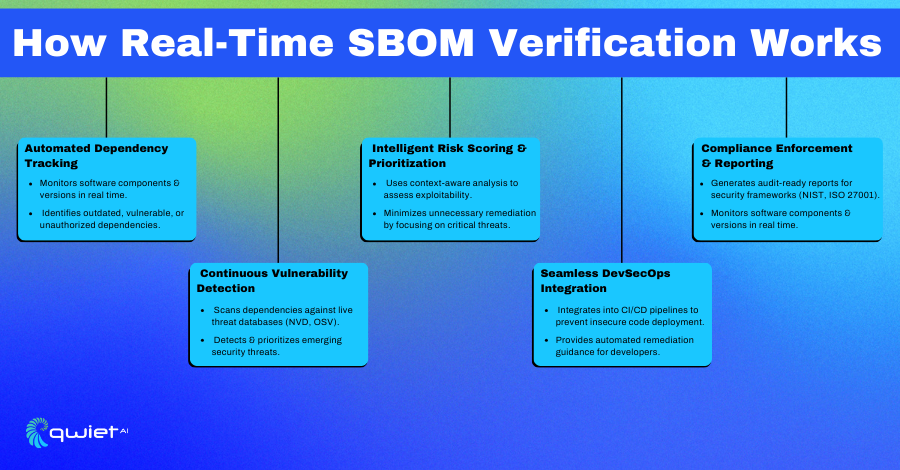
Automated Dependency Tracking
Automated dependency tracking monitors changes in software components and versions as they happen, providing real-time insights into your codebase. It helps identify outdated, vulnerable, or unauthorized dependencies early on, allowing teams to address potential issues before they impact the application. This constant visibility ensures that no dependency is overlooked.
Continuous Vulnerability Detection
Continuous vulnerability detection checks SBOM data against live databases like NVD, OSV, and other private threat intelligence sources. It scans for emerging security threats and prioritizes them based on severity and relevance. This proactive detection helps security teams stay ahead by identifying vulnerabilities as soon as they are disclosed.
Intelligent Risk Scoring and Prioritization
Intelligent risk scoring goes beyond simply listing vulnerabilities by analyzing their context and potential exploitability. This process assigns risk levels to vulnerabilities, allowing teams to focus on critical threats while minimizing unnecessary remediation efforts. Highlighting the issues that matter most optimizes security operations and saves time.
Seamless DevSecOps Integration
Real-time SBOM verification, seamlessly integrated into CI/CD pipelines, prevents deploying insecure code. It also provides developers with automated remediation guidance, helping them quickly address vulnerabilities without slowing development. This approach keeps security tightly aligned with development workflows.
Compliance Enforcement and Reporting
Compliance enforcement and reporting generate detailed security reports aligned with industry standards like NIST, ISO 27001, and emerging SBOM-related regulations. These reports are always audit-ready, reducing the effort needed for compliance assessments. Automated policy enforcement ensures that best practices are consistently applied across all projects, helping organizations comply with minimal overhead.
Conclusion
Traditional SBOMs offer only static snapshots, blinding security teams to new vulnerabilities that arise after the initial scan. Real-time SBOM verification solves this by continuously monitoring software dependencies, and improving security and compliance. AI-driven, context-aware approaches like Qwiet AI’s Code Property Graph (CPG) analysis further enhance accuracy by reducing false positives and helping teams focus on real threats. Ready to experience how real-time SBOM verification can transform your security strategy? Book a demo today.
FAQ
What is Real-Time SBOM Verification?
It’s a continuous process that monitors and validates software dependencies for new vulnerabilities, license issues, and security risks, ensuring up-to-date risk management beyond static SBOMs.
Why is Real-Time SBOM Verification better than traditional SBOMs?
Traditional SBOMs offer a one-time snapshot, missing new vulnerabilities. Real-time verification provides continuous monitoring, helping teams respond to emerging risks immediately.
How does Real-Time SBOM Verification help with compliance?
It supports standards like NIST and ISO 27001 and generates audit-ready reports, simplifying compliance with automated policy enforcement.
What is the role of AI in Real-Time SBOM Verification?
AI prioritizes real risks, reduces false positives, and uses context-aware analysis—like Qwiet AI’s CPG-based approach—to improve accuracy and efficiency.
Can Real-Time SBOM Verification be integrated into DevSecOps?
Yes, it integrates with CI/CD pipelines, providing real-time security insights and automated remediation without slowing development.
Read Next
Interactive Application Security Testing (IAST) Overview
What is Interactive Application Security Testing (IAST)? Interactive Application Security Testing (IAST) analyzes an application’s security while actively running. Unlike other approaches, it integrates directly with the app, allowing it to spot vulnerabilities as the code executes. This gives more accurate insights than methods that only look at static code or run tests outside the […]
SBOM Compliance Simplified: What U.S. Companies Need to Know
Introduction A Software Bill of Materials (SBOM) is like a detailed list of all your software’s components, licenses, and dependencies. It helps you see exactly what’s in your software and manage potential risks more effectively. As cybersecurity threats grow and regulations tighten in the U.S., SBOM compliance is becoming a top priority. From government mandates […]
Vulnerability Assessment Overview
What is a Vulnerability Assessment? A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can […]