What is Secure Development Lifecycle (SDL)?
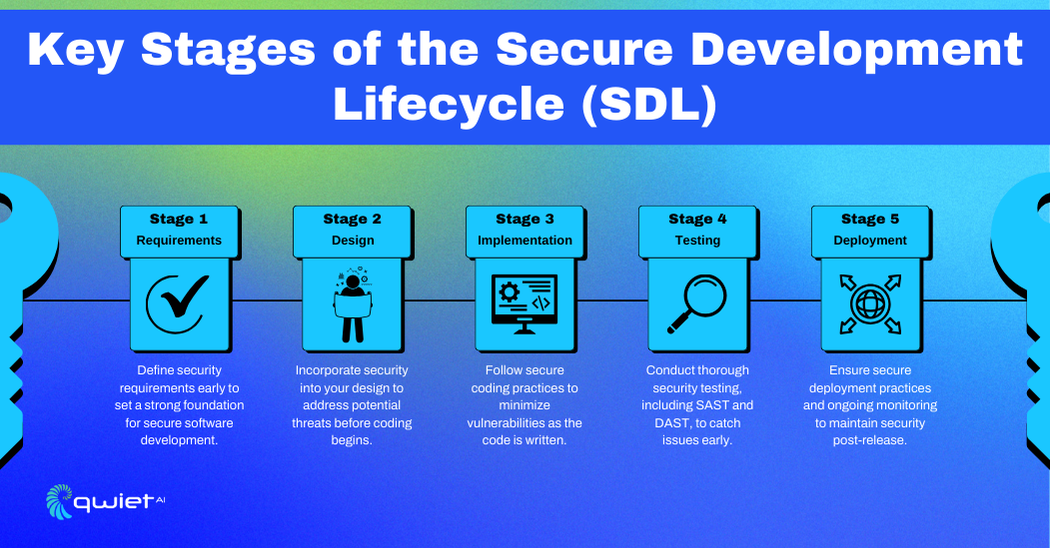
The Secure Development Lifecycle (SDL) framework incorporates security practices at every step of the software development process. Its goal is to reduce security risks by ensuring security is addressed from the beginning through the software’s final release.
SDL includes several stages, each with specific actions to address security:
- Requirements Phase: Security needs are identified and defined to ensure the project starts with a clear security foundation.
- Design Phase: Threat modeling is used to identify potential security risks and plan how to mitigate them.
- Implementation Phase: Secure coding practices are followed to prevent introducing vulnerabilities during the development process.
- Testing Phase: Security testing tools like SAST, DAST, and penetration testing are used to detect vulnerabilities before deployment.
- Deployment and Post-Deployment Phase: Continuous monitoring and regular updates are performed to maintain security and address new threats after release.
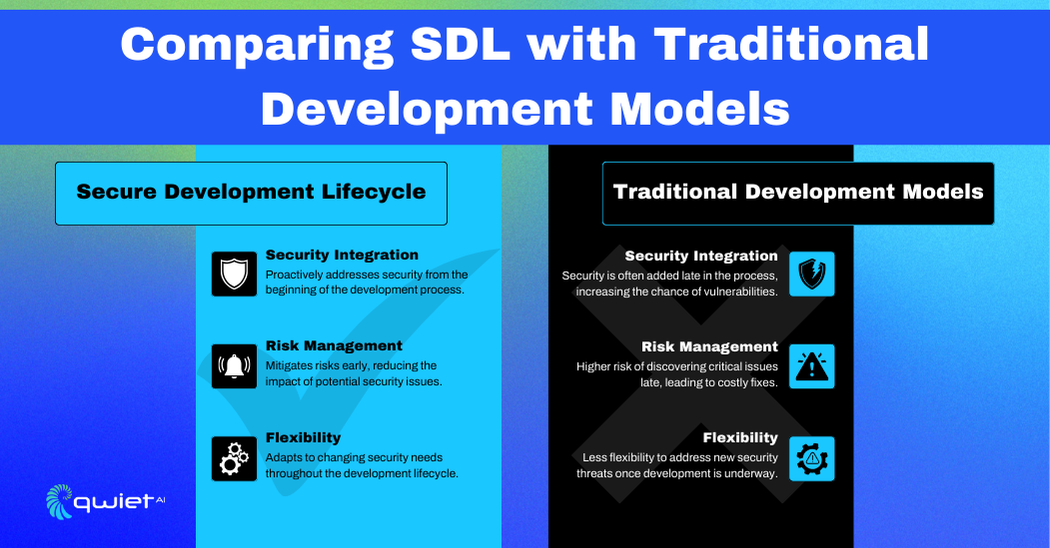
Unlike traditional development models, SDL incorporates security from the start rather than waiting until later stages like testing or after launch. Traditional models often focus on functionality first, with security being addressed as an add-on. On the other hand, SDL builds security into every phase, helping to produce more secure software from day one.
Importance of SDL in Software Development
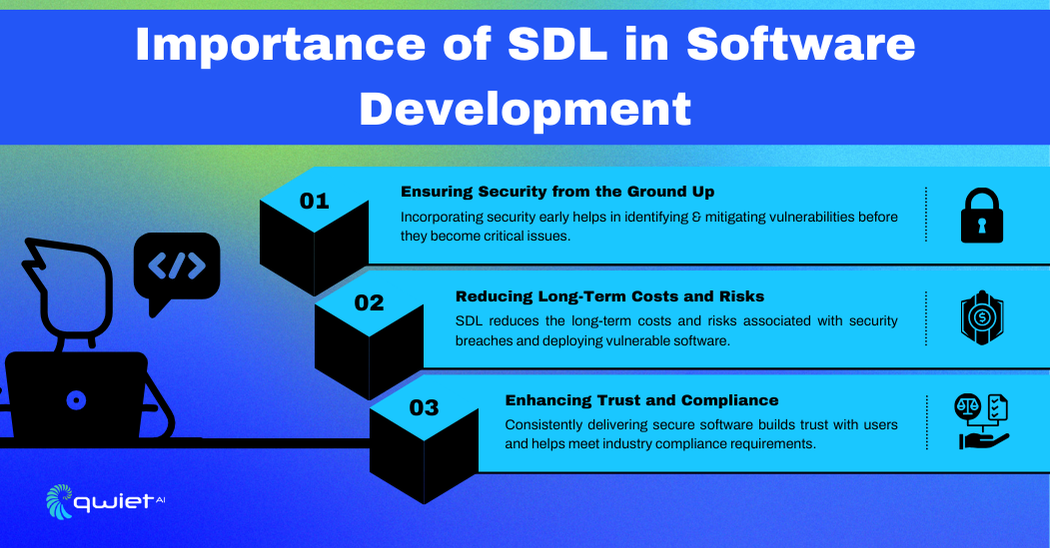
Security from the Ground Up
Incorporating security early in development helps identify and fix vulnerabilities before they become serious issues. By focusing on security from the start, teams can detect risks at each stage, reducing the chance of major problems later on. This proactive approach makes the software more secure and resilient against potential threats.
Reducing Long-Term Costs and Risks
SDL helps lower long-term costs by addressing security issues during development rather than after deployment. Catching vulnerabilities early is more cost-effective and prevents the expensive fixes that come with security breaches. It also minimizes the risk of deploying software with hidden flaws that could lead to costly incidents.
Enhancing Trust and Compliance
SDL helps build trust with users by consistently delivering software that meets security and industry compliance standards. Integrating security throughout development demonstrates a commitment to producing reliable and secure software, helping organizations meet legal requirements and maintain strong customer relationships.
Key Components of SDL
Security Requirements
Identifying and defining security requirements at the beginning of a project helps establish a strong foundation for secure software development. Early definition ensures the project is built with security, reducing the chance of introducing vulnerabilities later.
Aligning security requirements with overall business objectives to strike a balance between security and functionality is important. This alignment helps create a secure, effective product that meets business needs without compromising usability or performance.
Threat Modeling
During the design phase, threat modeling is critical to identify potential security threats and assess their impact. It helps teams pinpoint areas where the software could be vulnerable, allowing them to plan how to address those risks before they become problems.
Threat modeling directly influences design decisions by helping to develop strategies that mitigate identified risks—incorporating threat modeling early on guides how the system should be structured to minimize exposure to potential threats.
Secure Coding Practices
Following secure coding practices helps prevent vulnerabilities from being introduced during development. Adhering to these practices throughout the coding process ensures that the software is built to resist common attacks like SQL injection and cross-site scripting.
Continuous training for developers on the latest secure coding techniques is essential to keeping them updated on new threats and best practices. This ongoing education helps developers write secure code that aligns with the evolving security landscape.
Security Testing
Security testing, such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and penetration testing, should be integrated throughout development. These tests catch vulnerabilities early, allowing them to be addressed before they become major issues.
Automated tools are effective for quickly identifying common vulnerabilities, while manual testing offers deeper analysis for more complex security issues. Combining both methods provides comprehensive coverage, ensuring no weak spots are left unchecked.
Deployment and Post-Deployment Security
Adopting secure deployment practices, like automated security checks in CI/CD pipelines and secure configuration management, helps reduce risks when the software is released. These practices safeguard the deployment process and ensure the software is delivered securely.
After deployment, continuous monitoring and regular updates are needed to maintain security over time. This ongoing vigilance helps detect and address emerging threats, keeping the software secure even after it’s life.
Types of SDL Models
Agile SDL
SDL can be adapted to fit within the Agile framework by incorporating security into each sprint. Security tasks like threat modeling or code reviews are integrated into the regular Agile cycles, ensuring security is continuously addressed alongside new features.
The fast pace of Agile development can make it challenging to incorporate detailed security steps. To balance speed and security, lightweight security checks and automated tools can be used, while specific sprints or iterations can be dedicated to addressing more in-depth security tasks.
Waterfall SDL
SDL fits well into the Waterfall model since both follow a linear, phase-based approach. Security can be addressed systematically at each stage, from requirements to design, development, testing, and deployment, allowing thorough security planning and execution.
The advantage of applying SDL in Waterfall is that it allows comprehensive security planning upfront. However, its linear nature can make it less flexible in responding to changing security needs or threats that arise later in development, compared to more iterative models like Agile.
Hybrid SDL
In hybrid models that combine Agile and Waterfall elements, SDL can be integrated by applying security practices in both iterative and linear parts of the project. This allows for continuous security adjustments during development sprints while addressing broader security requirements in key project phases.
To effectively implement SDL in hybrid environments, teams should use flexible security strategies that adapt to iterative and phase-based development. Automated security checks can handle ongoing tasks, while detailed security reviews can be scheduled during major project milestones, ensuring security stays a priority without slowing development.
Conclusion
SDL is a framework that integrates security at every stage of software development, from defining requirements to post-deployment monitoring. Addressing security early and throughout the process helps reduce risks, cut long-term costs, and ensure compliance with industry standards. Whether you’re working in Agile, Waterfall, or Hybrid models, SDL can adapt to fit your development environment, ensuring a secure outcome. Incorporating SDL strengthens your software, minimizes vulnerabilities, and builds trust with users. To take the next step in improving your application security, book a demo with Qwiet today.
Read Next
Vulnerability Assessment Overview
What is a Vulnerability Assessment? A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can […]
Penetration Testing (Pentesting) Overview
What is Penetration Testing? Penetration Testing, or pen testing, is a security practice where experts try to break into your system, network, or application to find weaknesses. This controlled attack helps organizations see where they are vulnerable and fix those issues before real hackers can exploit them. The main goal of penetration testing is to […]
Threat Modeling
What is Threat Modeling? Threat modeling is a way to find and fix potential security problems in a system. We can understand how attackers might take advantage of these issues by looking at how the system is built and spotting weak points. This helps us get a clear view of the system’s security and identify […]