What is Security Awareness and Training?

Security awareness and training is a structured approach to educating employees, contractors, and stakeholders on cybersecurity best practices, common threats, and specific organizational policies. The goal is to increase understanding and awareness to help reduce security risks related to human behavior. With this knowledge, individuals become better equipped to recognize potential security threats, make safer choices, and contribute to the organization’s overall security.
Security awareness programs address phishing detection, password management, and proper data handling. These topics are tailored to the organization’s unique needs, making the training relevant and effective for different roles and departments. Security awareness and training aim to empower people within an organization to recognize and respond effectively to security threats. This proactive approach helps to strengthen the organization’s security posture by transforming employees into an informed first line of defense against potential attacks.
Why Security Awareness and Training Matters
Security
Human error plays a major role in security breaches, with phishing and social engineering attacks often targeting employees as entry points. Attackers exploit common mistakes, making it easy to bypass technical safeguards if people are unprepared. By educating employees on how to spot and report suspicious activities, organizations can reduce these risks significantly and address vulnerabilities that technology alone may not cover.
A well-trained workforce is a valuable asset in cybersecurity. It acts as a frontline defense against threats like data breaches, malware infections, and unauthorized access. With the right training, employees become better equipped to handle potential threats and to contribute actively to the organization’s security.
Stability & Performance
Reducing security incidents tied to human error directly impacts operational stability. Fewer incidents mean less downtime and fewer disruptions, which keeps the organization running smoothly. For IT teams, fewer security events free up time to work on proactive improvements and strategic initiatives rather than constantly responding to crises.
Regular training fosters a security-focused mindset across the organization, leading to better decision-making at all levels. This culture shift improves performance, as everyone—from entry-level to executive—becomes more aware of their role in protecting the organization.
Compliance
Security awareness and training are not just good practices; in many industries, they are regulatory requirements. Standards like HIPAA for healthcare, PCI-DSS for payment card data, and GDPR for data protection mandate regular employee training and require documentation of these efforts. Meeting these standards often includes proving that employees are regularly trained in security.
A formal training program supports compliance and helps organizations avoid potential fines and maintain a strong reputation with customers and partners. Meeting these compliance requirements shows a commitment to security that enhances trust and aligns with industry standards.
Components of Security Awareness and Training
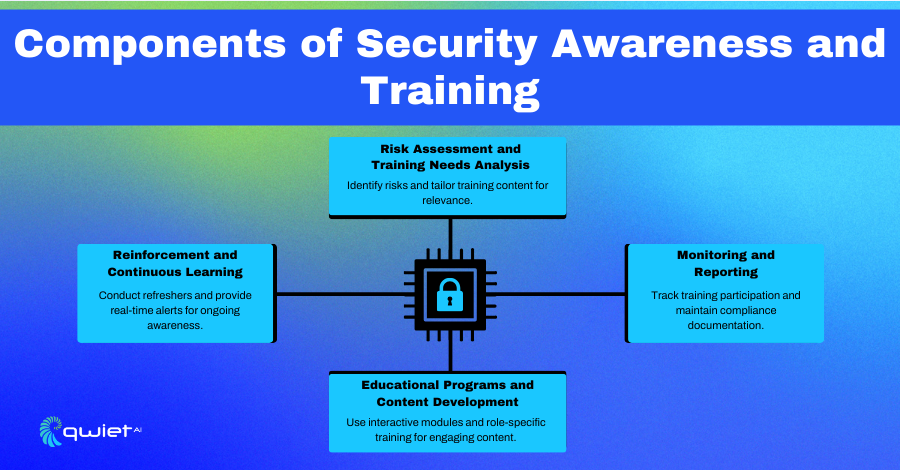
Risk Assessment and Tailored Training
A successful security awareness program begins with identifying specific threats, such as phishing, social engineering, and data leaks, that employees are likely to face. Tailoring training content by role and department makes the material more relevant and effective. For example, phishing simulations allow employees to practice recognizing suspicious emails, while interactive modules—including videos, quizzes, and real-world scenarios—enhance engagement and help employees retain essential security skills.
Reinforcement and Continuous Learning
Building a security-conscious culture requires ongoing reinforcement. Regular refresher courses keep employees updated on emerging threats, while security awareness campaigns through posters, emails, and newsletters serve as daily reminders of best practices. Real-time alerts about active threats, such as new phishing campaigns, keep employees vigilant and prepared to respond effectively to immediate risks.
Monitoring, Reporting, and Compliance
Tracking training participation and assessing its effectiveness help ensure that security training reaches every employee and that they retain key concepts. Compliance documentation records training activities, supports audits, and demonstrates adherence to regulatory standards. This documentation provides transparency and accountability, ensuring that the organization’s security practices align with industry requirements and are continually improved to address evolving threats.
Conclusion
Security awareness and training are powerful tools for minimizing human error and building a proactive defense against evolving threats. But even the most trained team needs strong, automated support to prevent vulnerabilities from entering your codebase. This is where Qwiet AI’s SAST (Static Application Security Testing) solution becomes invaluable. By integrating SAST with a security-aware workforce, you create a dual approach to protecting your applications: employees are equipped to recognize threats, and your code is continuously scanned to detect vulnerabilities before they reach production.
If you’re ready to combine security training with advanced application testing, book a call with Qwiet AI today.
Read Next
Microservices Security Overview
What is Microservices Security? Microservices security is the comprehensive approach to safeguarding each service within a microservices architecture. In this model, each service functions independently, which creates unique security requirements for each one. To secure these distributed services, microservices security involves methods to protect inter-service communications, secure APIs, and manage access and identity across multiple […]
Cybersecurity Compliance and Why it Matters
What is Cybersecurity Compliance? Cybersecurity compliance means following the rules, standards, and best practices that help protect your information systems and data from cyber threats. These regulations outline the minimum security steps organizations need to take to keep sensitive information safe and ensure their systems are secure and reliable. Sticking to compliance and regulatory requirements […]
Interactive Application Security Testing (IAST) Overview
What is Interactive Application Security Testing (IAST)? Interactive Application Security Testing (IAST) analyzes an application’s security while actively running. Unlike other approaches, it integrates directly with the app, allowing it to spot vulnerabilities as the code executes. This gives more accurate insights than methods that only look at static code or run tests outside the […]