What is Security by Design?

Security by Design is a proactive approach that gives developers a sense of control by integrating security measures into every stage of the software development process. Instead of treating security as an afterthought, this methodology ensures that security considerations are embedded from the initial design phase to deployment and maintenance. The goal is to create secure systems by default, minimizing vulnerabilities and reducing the risk of exploitation.
Integrating security from the beginning of the development process is important because it helps identify and address potential security issues early rather than reacting to them after they occur.
This approach leads to more resilient and trustworthy systems, providing a sense of security and peace of mind. It reduces the cost and complexity of implementing security measures later, and ensures compliance with regulatory requirements. Organizations can build stronger, more secure applications and infrastructure by prioritizing security from the start.
Key Principles of Security by Design
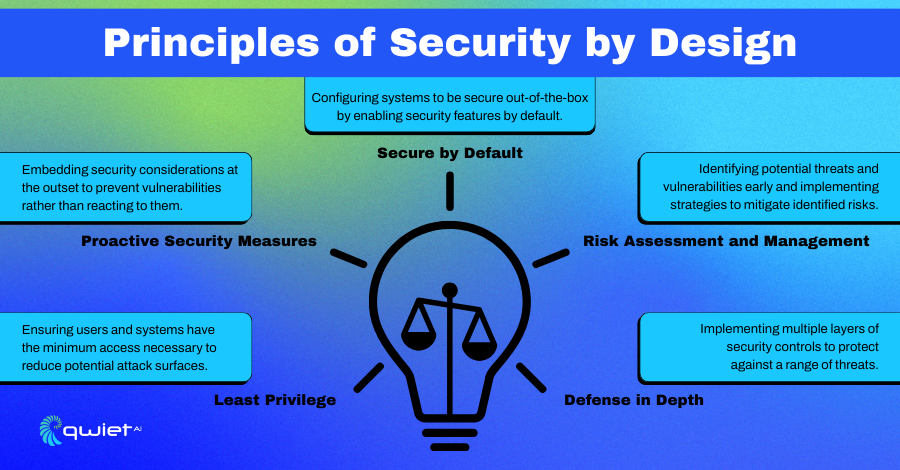
Proactive Security Measures
Embedding security considerations at the outset means integrating security practices right from the beginning of the development cycle. This helps identify and address potential issues early, making the system more secure as it evolves.
Preventing vulnerabilities rather than reacting to them involves identifying and mitigating potential security risks before they can be exploited. By focusing on prevention, you can significantly reduce the likelihood of security incidents and minimize the impact of any issues that do arise.
Risk Assessment and Management
Identifying potential threats and vulnerabilities early is crucial for effective security management. By assessing risks at the start, you can clearly understand where your system might be vulnerable and prioritize your security efforts accordingly.
Implementing strategies to mitigate identified risks involves developing and deploying measures to address the vulnerabilities and threats you’ve identified. This might include applying patches, configuring security settings, or developing new security features to protect your system.
Least Privilege
Ensuring users and systems have the minimum access necessary means granting only the permissions needed to perform their tasks. This helps limit the potential damage that could be caused by a compromised account or system.
Reducing potential attack surfaces involves minimizing the number of ways an attacker could gain unauthorized access to your system. This includes closing unnecessary ports, removing unused services, and only exposing essential components.
Defense in Depth
Implementing multiple layers of security controls provides a comprehensive approach to protecting your system. Using a combination of security measures, you can create multiple barriers that an attacker would need to bypass, making it more difficult for them to succeed.
Protecting against f threats ensures that your system is safeguarded from attacks. This includes using firewalls, intrusion detection systems, and encryption to defend against vulnerabilities.
Secure by Default
Configuring systems to be secure out-of-the-box means setting default configurations that prioritize security. This reduces the likelihood of vulnerabilities being introduced due to misconfigurations or oversight during setup.
Enabling security features by default ensures that the most important security measures are active from the start. This includes features like automatic updates, secure authentication methods, and default encryption settings, which help protect your system without requiring additional configuration.
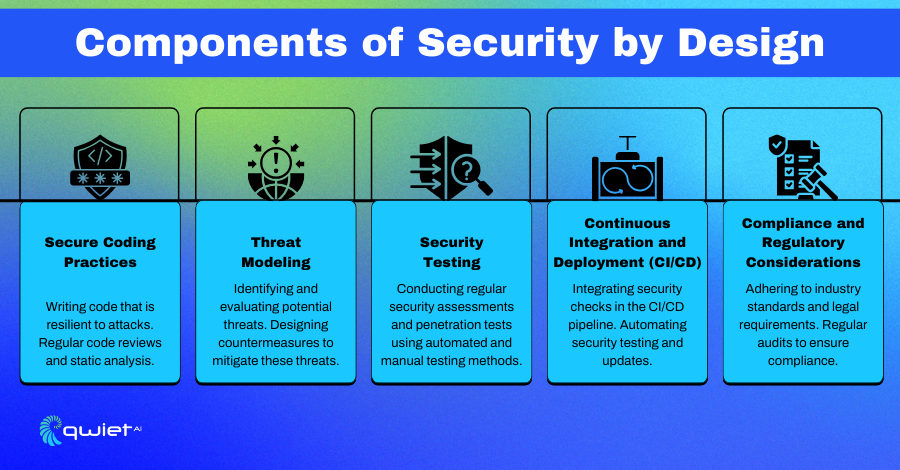
Benefits of Security by Design
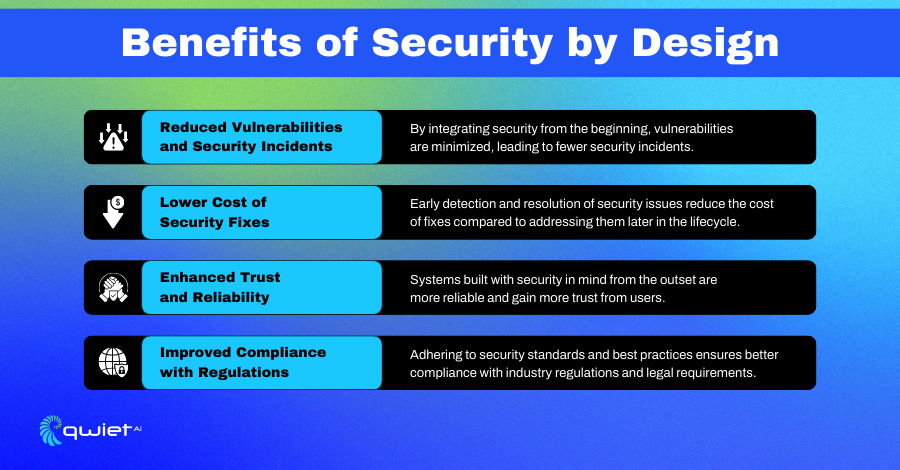
Reduced Vulnerabilities and Security Incidents
Implementing Security by Design helps to minimize the number of vulnerabilities and security incidents. By embedding security measures throughout the development process, potential weaknesses are identified and addressed early, leading to a more secure system. This proactive approach reduces the likelihood of breaches and mitigates the impact of any incidents.
Lower Cost of Security Fixes Due to Early Detection
Detecting security issues early in the development cycle leads to significantly lower costs for fixing them. When vulnerabilities are found and resolved during development, addressing them after deployment requires fewer resources and less effort. This saves money and helps avoid potential disruptions to business operations.
Enhanced Trust and Reliability of Systems
Security by Design enhances the trust and reliability of your systems. When security is a fundamental part of the development process, it results in more robust and dependable systems. This builds confidence among users and stakeholders, knowing that the system is designed to protect their data and ensure smooth operations.
Improved Compliance with Regulations
Following Security by Design principles helps ensure compliance with industry standards and regulations. By integrating security practices from the beginning, you can more easily meet regulatory requirements and pass audits. This avoids potential legal issues and demonstrates your commitment to maintaining high-security standards.
Conclusion
Security by Design means building security into every step of your software development process, making your systems secure from the get-go. By tackling vulnerabilities early, you reduce risks and save on costly fixes. This proactive approach strengthens your security, boosts user trust, and helps you stay compliant with regulations. Want to see how you can seamlessly integrate security into your development process? Book a demo with Qwiet to learn more.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
