Introduction
Every developer craves building applications that offer stellar functionalities. But equally, if not more, crucial is ensuring that these applications are built on a bedrock of security. Today, we’ll unravel one of the more notorious vulnerabilities plaguing the web – Cross-Site Scripting (XSS). In particular, we’ll dissect its most treacherous variant: the DOM-based XSS.
For the uninitiated, Cross-Site Scripting is a type of web vulnerability where attackers inject malicious scripts into web pages that other users view. These scripts can access any cookies, session tokens, or additional sensitive information retained by browsers, leading to data theft or even malicious actions executed on behalf of the user.
Deep Dive into DOM-based XSS Attacks
The DOM (Document Object Model) represents the page’s structure, allowing scripts to modify its content, structure, and styling. DOM-based XSS attacks target this very foundation. Unlike traditional XSS attacks where the server stores or reflects the payload, in DOM-based XSS, the client-side scripts in the page itself execute the malicious payload.
Let’s delineate the types of XSS:
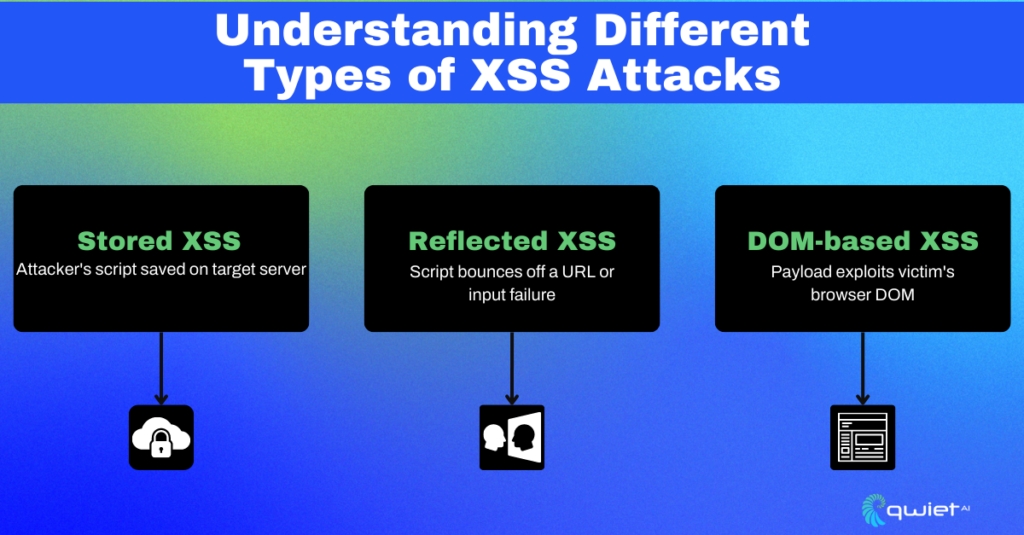
- Stored XSS: The malicious script injected by the attacker is permanently stored on the target server.
- Reflected XSS: The injected script is reflected off a web server via a URL, a failed input validation, or another vector.
- DOM-based XSS: The payload is executed due to modifying the DOM in the victim’s browser.
Now, let’s see a vulnerable code snippet:
// Vulnerable code to DOM-based XSS
| const userText = window.location.hash.substring(1); document.write(userText); |
In this code, content from the URL after the hash symbol (#) is directly rendered into the page using document.write(). If an attacker appends a malicious script to the URL after the #, it would be executed.
Common Attack Vectors in DOM-based XSS
Attackers manipulate the DOM structure or inject malicious scripts via user inputs, URL fragments, or other client-side objects. Imagine a web page using URL parameters to display content without proper validation.
Typical payloads might look like:
| // Malicious URL fragments #<script>alert(‘xss’)</script> #<img src=x onerror=alert(‘xss’)> |
These scripts, when executed, will run the injected code (in these cases, triggering alert pop-ups), demonstrating a successful XSS attack.
Identifying Vulnerabilities: Tools and Techniques
Modern browsers come armed with developer tools that can prove invaluable in pinpointing insecure DOM manipulations. For instance:
| // In Chrome DevTools console document.querySelector(‘vulnerable-element’).outerHTML; |
The above command fetches the outer HTML of a suspicious element, possibly revealing insecure DOM alterations.
However, manually trawling through complex applications isn’t feasible. This is where automated scanners come in. Tools like OWASP ZAP and Burp Suite are adept at scanning applications for vulnerabilities, including XSS. But no tool is foolproof. Hence, regular penetration testing, where ethical hackers try to exploit your system, provides invaluable insights into real-world vulnerabilities.
Mitigation Strategies for DOM-based XSS Attacks
User input should never be trusted blindly. Validating and sanitizing inputs can thwart a myriad of attacks:
| // Input validation and sanitization in JavaScript const sanitizeString = str => { const temp = document.createElement(‘div’); temp.textContent = str; return temp.innerHTML; }; |
This simple function uses a DOM method to neutralize potentially harmful characters in user inputs.
Content Security Policy (CSP), a tool lesser known outside the security circles, is a silent guardian. By setting up HTTP headers that dictate what resources a browser should be allowed to load, CSP significantly curtails XSS risks:
| // Example CSP header to only allow scripts from the same origin Content-Security-Policy: script-src ‘self’ |
Using established JavaScript frameworks securely can reduce the risk. For instance, React and Angular have built-in mechanisms that automatically escape content, ensuring that malicious payloads don’t get executed:
| // Safe DOM manipulation in React const userInput = ‘<script>maliciousCode()</script>‘; return <div>{userInput}</div>; |
In React, JSX content gets automatically escaped, rendering the script harmless.
Advanced Considerations in DOM-based XSS Protection
The dynamism of web technologies ensures that DOM-based XSS vectors continue evolving. Regularly updating software, frameworks, and libraries is imperative. While tools and automated checks are essential, a culture of security awareness encompassing developers, QA teams, and beyond fortifies your application’s defense.
For more advance considerations you might want to implement the below:
- Real-time Monitoring and Logging: The onset of an attack can often be detected through suspicious patterns in real-time logging. Having mechanisms that monitor and alert based on irregular DOM manipulations can be crucial in identifying and thwarting potential attacks.
- Input and Output Encoding: Sanitizing inputs isn’t enough. Consider how data is output. Properly encoding data before rendering it ensures that even if an attacker manages to insert a malicious payload, it won’t be executed as intended.
- Adoption of Strict Type Checks: If a function expects a number, ensure that only one can be passed. Libraries such as TypeScript can assist in ensuring type safety in JavaScript applications, which can aid in reducing vulnerabilities.
- Web Workers and Sandboxing: Consider executing code in a Web Worker or in a sandboxed iframe. By isolating potentially harmful scripts from the main application, you can prevent access to the main DOM or sensitive user data.
- Strict CSP Policies: While the introductory section touched upon CSPs, adopting more stringent policies like nonce-based or hash-based source whitelists can be invaluable. This ensures that only scripts with the correct nonce or hash value can be executed, even if an attacker tries to inject a malicious script.
- Avoid DOM APIs Prone to XSS: Instead of risky methods like document.write(), element.innerHTML, or eval(), opt for safer alternatives like element.textContent, Node.appendChild(), or JSON.parse().
- Integrate Security into CI/CD: Automate security checks with a tool like Qwiet in your Continuous Integration/Continuous Deployment pipelines. This ensures that every piece of code is checked for potential vulnerabilities before it reaches the production environment.
Conclusion
Vigilance is paramount in web development, where DOM-based XSS attacks lurk in shadowed corners. As we’ve explored, recognizing and mitigating these threats is crucial, but even the most vigilant can benefit from expert guidance. Utilizing a tool like Qwiet AI helps to proactively identify such vulnerabilities up front, bridging the gap between awareness and action. If you’re serious about bolstering your web app security, a conversation with Qwiet AI might be the most prudent next step. Book a call with our team today.