Introduction
Are you confident that your Python application can stand up to the latest cybersecurity threats? As Python’s popularity surges across various fields, the security of its codebases has become critical. This article delves into essential security practices for Python developers, aiming to fortify applications against cyber threats. You’ll walk away with a clear understanding of common vulnerabilities, strategies to address them, and a wealth of Python-specific security measures to apply to your projects.
The Security Landscape in Python Development
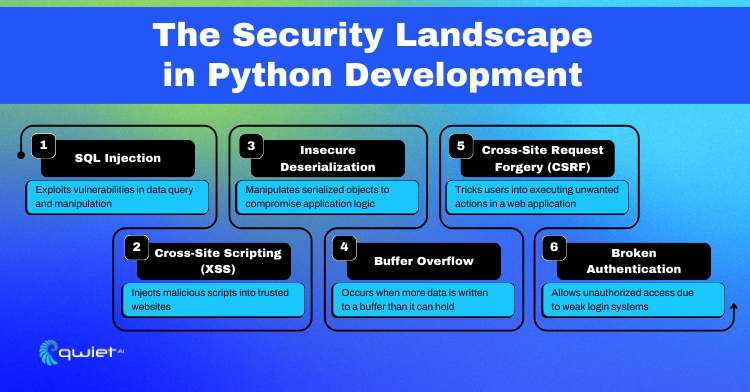
Python is a powerhouse in the programming world, but it’s not immune to security risks. When we talk about coding in Python, the threat list is long: we’ve got everything from injection attacks to authentication issues. These aren’t just small bugs; they can lead to serious breaches, leak sensitive data, and give cyber intruders the keys to the kingdom. Python developers need to stay sharp and secure their code from these vulnerabilities.
Some of the common vulnerabilities include:
- SQL Injection: In Python, this risk emerges when executing SQL commands with user input not correctly sanitized, potentially corrupting or leaking database data.
- Cross-Site Scripting (XSS): Python web apps face this when user-generated content isn’t escaped properly, leading to the execution of malicious scripts.
- Insecure Deserialization: Python applications can be compromised if they deserialize data from untrusted sources with modules like pickle.
- Buffer Overflows: A less common issue in Python due to its high-level nature, but it can occur in extensions written in C or when interfacing with lower-level libraries.
- Cross-Site Request Forgery (CSRF): Python frameworks often include CSRF protection. Still, developers need to ensure this is enabled and properly configured to prevent unauthorized actions on behalf of logged-in users.
- Broken Authentication: Weak implementation of session management and user authentication in Python can allow attackers to assume users’ identities.
Secure coding in Python development is all about writing code that’s not just functional but also safe. As developers, we must think like an attacker and defend against potential threats. This means rigorously validating all inputs to prevent SQL injection and XSS attacks, carefully handling errors so they don’t give away system information, and ensuring that authentication methods are airtight to keep out unauthorized users.
Python Input Validation
Input validation is the first line of defense in Python programming. It ensures that the data your program receives is what it expects and can safely process. This step is important because invalid or malicious data can lead to security vulnerabilities, such as SQL injection or buffer overflows. In essence, input validation is about preemptively catching errors and potential exploits by checking the data before it’s used in your application.
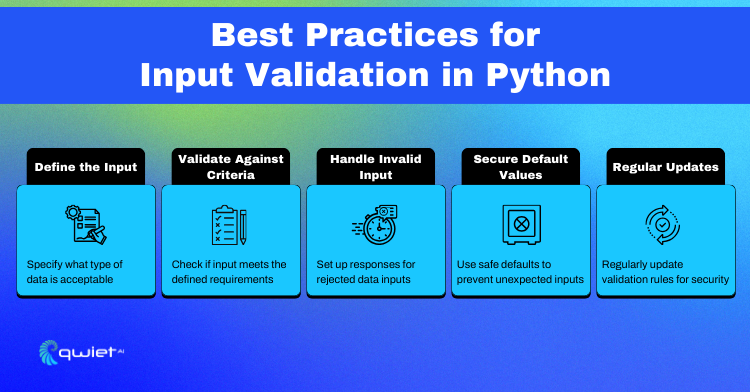
Here’s a rundown of the best practices for input validation in Python:
- Define the Input: Clearly define what kind of data is acceptable. If it’s a string, should it be alphanumeric? If it’s a number, what range is okay?
- Validate Against Criteria: Always check that the incoming data matches your requirements. This isn’t just about type checking; it’s about confirming the data fits the expected format and length and adheres to the expected pattern.
- Handle Invalid Input: When data doesn’t pass validation, have a plan. You might log the issue, throw an exception, or ask the user to re-enter the data, but don’t just let it slide.
- Secure Default Values: Use safe default values to handle unexpected inputs. If something slips through the cracks, your application won’t suddenly behave unpredictably.
- Regular Updates: Keep your validation logic up-to-date. As new threats emerge, you must adjust your rules to stay one step ahead of attackers.
So, how would we implement the above practices let take a look:
| def validate_input(data, data_type, constraints): “”” A generic input validation function that demonstrates best practices. :param data: The input data to be validated :param data_type: The type the input data should be (e.g., int, str) :param constraints: A dictionary of constraints (e.g., {“min”: 10, “max”: 100}) :return: Validated data or raises an exception if invalid “”” # Define the input: Ensure the type matches what’s expected if not isinstance(data, data_type): raise TypeError(f”Input must be of type {data_type.__name__}”) # Validate against criteria: Check the data against provided constraints if data_type == int and (“min” in constraints or “max” in constraints): if constraints.get(“min”) is not None and data < constraints[“min”]: raise ValueError(f”Input must be at least {constraints[‘min’]}”) if constraints.get(“max”) is not None and data > constraints[“max”]: raise ValueError(f”Input must be no more than {constraints[‘max’]}”) # Additional checks can be added here for other data types and constraints # If the data passes all checks, return the data return data # Example usage try: age = validate_input(data=25, data_type=int, constraints={“min”: 18, “max”: 99}) print(f”Validated age: {age}”) except (TypeError, ValueError) as e: print(f”Invalid input: {e}”) # Handle invalid input: Set a secure default value or prompt for re-entry age = 18 # Secure default value if input is not valid |
As you can see from the above snippet, the validate_input function is designed to be versatile, handling various types of data and constraints. It begins by confirming that the data matches the expected type, preventing type-related errors. It then applies specific constraints, like minimum and maximum values for integers, which is crucial for numerical validations. If the input doesn’t meet the criteria, it raises an appropriate exception, clearly communicating the nature of the issue.
We attempt to validate an age integer, ensuring it falls within a legal range. We catch the exception if the input is invalid and print an error message. As a fallback, we set a secure default age value, maintaining the application’s integrity in case of invalid input. This demonstrates handling unexpected or unsafe inputs in a controlled manner, ensuring the application remains stable and secure.
Error Handling and Logging
- Strategies for secure error handling.
- Best practices for logging errors without exposing sensitive information.
- Python code examples.
Error handling in Python is more than just preventing crashes; it’s about ensuring that they do so without compromising security when things go wrong. Secure error handling means anticipating the unexpected and having a strategy to deal with it.
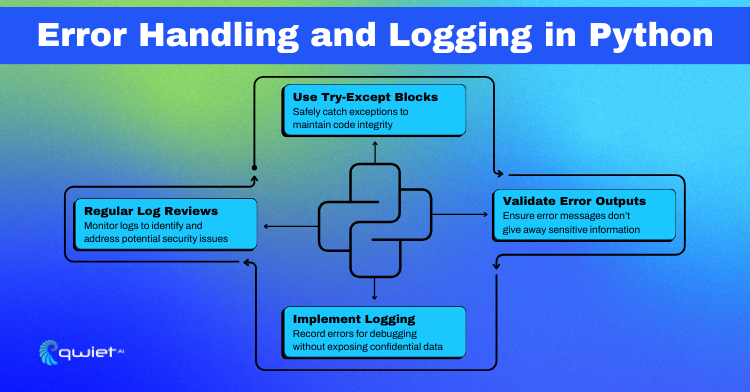
Using try-except blocks is the first step, allowing you to catch and respond to exceptions in a way that keeps your application running smoothly and securely. It’s essential to anticipate and handle specific exceptions to prevent a generic catch-all that might swallow important debugging information or security-relevant signals.
The goal of logging errors is to record enough information for debugging while not leaking any sensitive details. This balance is critical:
- Validate Error Outputs: Always sanitize error messages displayed to the user or written to logs to prevent revealing stack traces, system information, or confidential data.
- Implement Logging: Use Python’s logging module to record errors. Configure it to exclude sensitive information and ensure that logs are stored securely and with proper access control.
- Regular Log Reviews: Review log files for anomalies that could indicate security incidents or operational issues. This practice is not just for post-mortem analysis but is a proactive security measure.
Here’s a Python snippet that demonstrates these practices:
| import logging from logging.handlers import RotatingFileHandler # Set up logging with a safe level of detail logger = logging.getLogger(__name__) logger.setLevel(logging.INFO) handler = RotatingFileHandler(‘app.log’, maxBytes=5000, backupCount=2) formatter = logging.Formatter(‘%(asctime)s – %(levelname)s – %(message)s’) handler.setFormatter(formatter) logger.addHandler(handler) def handle_division(dividend, divisor): try: result = dividend / divisor except ZeroDivisionError as e: # Validate error output: Don’t give away details, just the necessary info logger.error(“ZeroDivisionError occurred: Division by zero attempt.”) # Handle invalid input: Provide a default value or re-prompt result = None # Secure default value except Exception as e: # Log the error with a safe level of detail for debugging logger.error(f”An error occurred: {str(e)}”) result = None return result # Use the function and log results result = handle_division(10, 0) if result is None: logger.info(“Result was set to None due to an error.”) |
This snippet uses a try-except block to handle any ZeroDivisionError specifically, which could occur during division operations. We log the error occurrence without exposing any sensitive details. For other unexpected exceptions, we catch them generally, log an error message, and set a secure default result value of None. This way, we’re recording the necessary debugging information without risking sensitive information. Regular review of the app.log file would help identify and rectify recurring issues while keeping an eye out for potential security threats.
Secure Authentication and Authorization
Authentication and authorization form the cornerstone of web security in Python applications. Authentication is about verifying who a user is, typically through credentials like usernames and passwords, while authorization determines what an authenticated user is allowed to do. Getting these processes right is essential to protect against unauthorized access and to ensure that users can only interact with the parts of your application they’re permitted to.
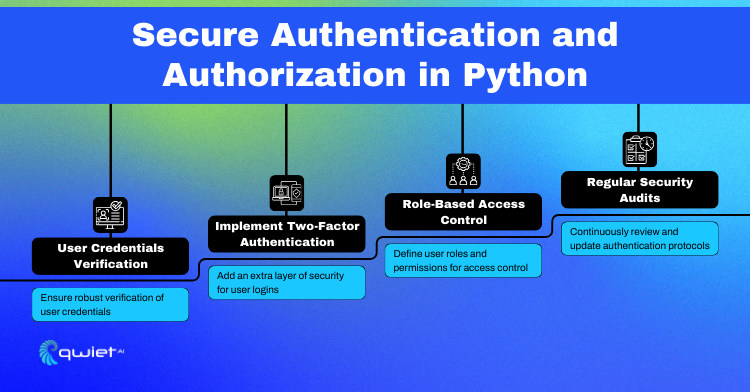
For secure user authentication in Python, follow these techniques:
- Strong Credential Storage: Use hashing algorithms, like bcrypt, to store user passwords. Never store passwords in plain text.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security, ensuring that even if a password is compromised, unauthorized access is still prevented.
- Session Management: Utilize secure, unique session tokens and ensure they are invalidated upon logout or after a period of inactivity.
Below is a Python code snippet that demonstrates secure authentication and role-based access control, typically in the context of a web application using Flask:
| from flask import Flask, request, redirect, render_template, session from flask_bcrypt import Bcrypt from flask_sqlalchemy import SQLAlchemy from itsdangerous import URLSafeTimedSerializer app = Flask(__name__) bcrypt = Bcrypt(app) db = SQLAlchemy(app) app.config[‘SECRET_KEY’] = ‘your-secret-key’ app.config[‘SQLALCHEMY_DATABASE_URI’] = ‘sqlite:///users.db’ login_serializer = URLSafeTimedSerializer(app.config[‘SECRET_KEY’]) # User model with role class User(db.Model): id = db.Column(db.Integer, primary_key=True) username = db.Column(db.String(80), unique=True, nullable=False) password = db.Column(db.String(120), nullable=False) role = db.Column(db.String(80), default=‘user’) # Default role is ‘user’ def set_password(self, password): self.password = bcrypt.generate_password_hash(password) def check_password(self, password): return bcrypt.check_password_hash(self.password, password) # Authentication @app.route(‘/login’, methods=[‘GET’, ‘POST’]) def login(): if request.method == ‘POST’: username = request.form[‘username’] password = request.form[‘password’] user = User.query.filter_by(username=username).first() if user and user.check_password(password): session[‘user_id’] = user.id session[‘token’] = login_serializer.dumps([user.username, user.role]) return redirect(‘/’) else: return ‘Invalid username or password’, 401 return render_template(‘login.html’) # Authorization @app.route(‘/admin’) def admin(): if ‘token’ in session: try: username, role = login_serializer.loads(session[‘token’], max_age=3600) if role == ‘admin’: return render_template(‘admin.html’) else: return ‘Unauthorized’, 403 except: # If the token is invalid or expired return ‘Unauthorized’, 403 return redirect(‘/login’) # Logout @app.route(‘/logout’) def logout(): session.pop(‘user_id’, None) session.pop(‘token’, None) return redirect(‘/login’) # Main page @app.route(‘/’) def index(): return ‘Welcome to the secure app!’ if __name__ == ‘__main__’: db.create_all() # Create database tables app.run(debug=True) |
This snippet provides a basic structure for handling secure user authentication and role-based access control within a Flask application. It includes user model definitions with roles, password hashing for secure credential storage, session management with secure token generation, and role verification for access control.
In the /login route, it handles user authentication by verifying usernames and passwords and storing a secure session token if successful. The /admin route demonstrates role-based access control, where only users with the ‘admin’ role can view the page, and the /logout route properly clears the session. Note that this is a simplified example for demonstration purposes, and a real-world application should include additional security measures such as HTTPS enforcement, proper error handling, and more sophisticated user session management.
Checklist to secure Python development
Securing your Python development process is an ongoing task involving multiple security layers. Here’s a checklist with specific practices that you can take to bolster the security of your Python application:
- Integrate a Python Security Linter: Incorporate a security-focused linter-like bandit into your CI/CD pipeline to catch security flaws.
- Automate Dependency Checks: Use safety to automatically check your installed dependencies for known security vulnerabilities.
- Implement Pre-Commit Hooks: Set up pre-commit hooks using pre-commit that run checks like flake8, black for code formatting, and sort for import sorting, which indirectly improves code quality and security.
- Use HTTPS for All Web Traffic: Ensure your Python web applications enforce HTTPS by default. When using Flask, you can redirect all incoming requests to HTTPS.
- Employ ORM for Database Interactions: Utilize Object-Relational Mapping (ORM) libraries like SQLAlchemy or Django ORM to interact with databases, which helps prevent SQL injection attacks.
- Store Secrets Securely: Use python-dotenv to load sensitive data from an .env file that is not tracked in version control systems.
- Enable ORM Debug Logging With Caution: In development, you might enable ORM debug logging to troubleshoot issues, but ensure it’s turned off in production to avoid leaking sensitive information.
- Regularly Rotate Encryption Keys: Make it a habit to rotate your encryption keys periodically. Implement key rotation in your application logic if you manage your encryption.
- Enforce Type Checking: Use mypy or similar tools to enforce type checking, which can prevent certain types of bugs that might lead to security vulnerabilities.
- Setup Structured Logging: Use structured logging with proper log levels, which helps diagnose issues without exposing too much information.
- Leverage Automated Security Scanning Tool: Use an automated security tool like qwiet to regularly scan your codebase for known vulnerabilities in both your code and dependencies. Set it up to run at regular intervals, such as with each commit or at least once a week.
Conclusion
We’ve journeyed through the crucial aspects of securing Python code, tackling input validation, error handling, authentication, and more, concluding with a targeted checklist to keep your codebase secure. Remember, security is an ongoing pursuit, and staying updated with best practices is key to defense.
Ready to enhance the security of your Python codebase? Book a demo with Qwiet today.