Our customers have repeatedly communicated a desire to deliver secure software without compromising software delivery timelines. At the same time, they have frequently reported that traditional software composition analysis (SCA) tools create an overwhelming number of open-source vulnerability tickets.
To quantify the problem, we ran an experiment with a cross-section of our customers. An analysis of 49 apps resulted in the discovery of 2,761 OSS vulnerabilities spread across 718 vulnerable packages. Of these vulnerabilities, most were eventually found to have no impact and therefore were dismissed as “low priority”—more colloquially known as “false positives.”
Our experiment reduced the time our customers spend chasing bugs by more than 90 percent. In the following blog, we break down the process in a way that anyone on your team should be able to follow. We also offer suggestions on alternatives to incumbent SCA tools.
What do we mean by “Reachable”?
Before we get started, let’s be clear about what we mean by “reachable.” If an attacker-controlled path exists that connects an insecure application input to common vulnerabilities and exposures (CVE) in a third-party library contained in the same application, then this CVE will be considered “reachable” in that app.
An attacker-controlled path is determined by tracing an application’s public inputs (or sources) to sensitive sinks (db, log, http, etc.), lacking any validation or sanitization routine between these sources, sinks. The analysis of the application is critical to identify reachable vulnerabilities.
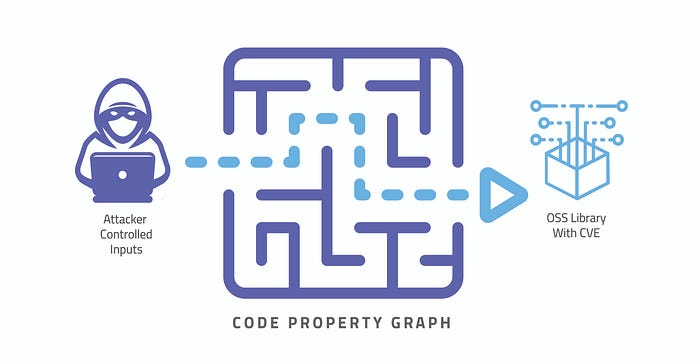
Any SCA solution that does not analyze the application and limits its analysis to merely the list of dependencies used by the application cannot conduct this analysis
How does Code Property Graph determine “Reachability”?
Qwiet AI’s perZero platform performs constituent analysis through the same Code Property Graph, whether it is identifying code vulnerabilities, OSS vulnerabilities, secrets, or security insights.
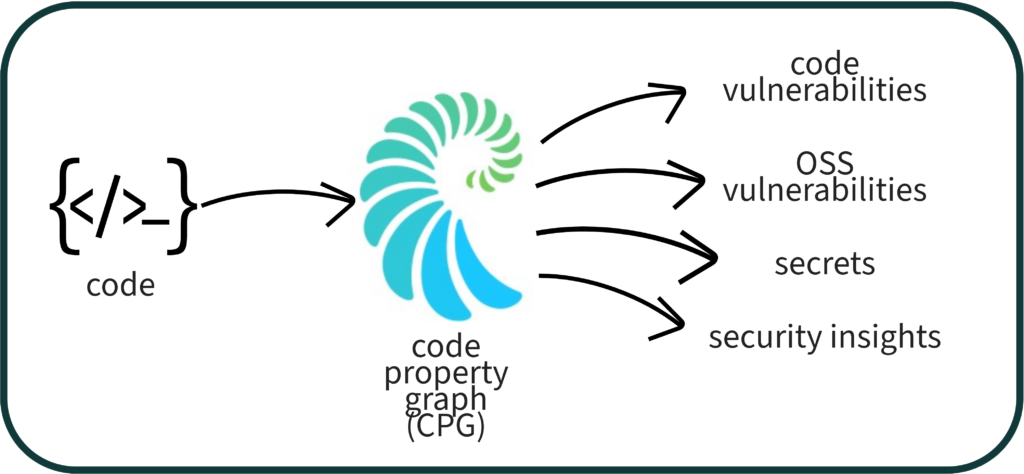
Analysis always starts with the construction of the Code Property Graph.
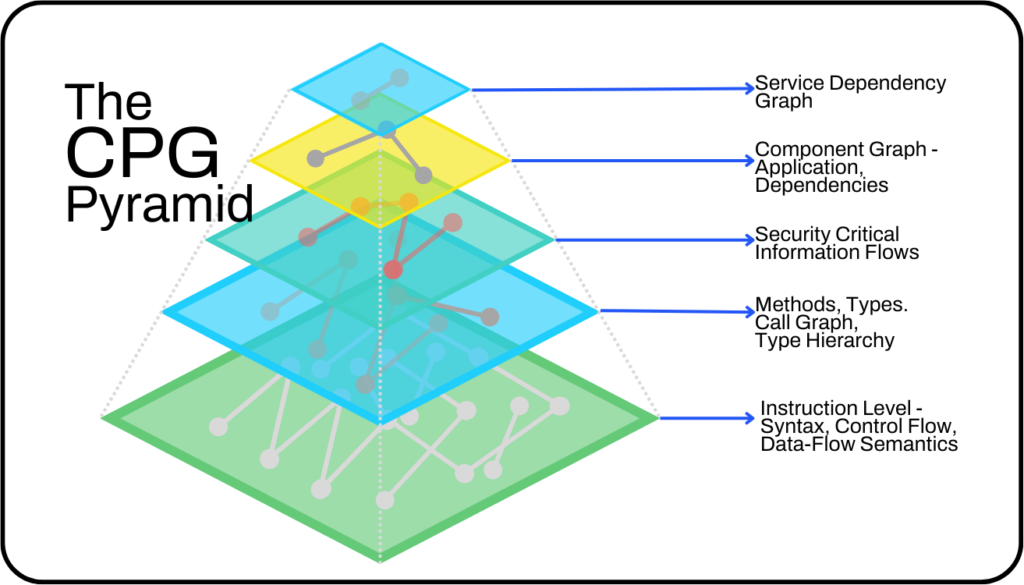
The Code Property Graph displays all code components and their inter-relationships. It contains everything a developer needs to identify reachable vulnerabilities. By showing the call graphs that connect application inputs to its sensitive sinks, it visually represents relationships of dependent components with application code.
Unlike other rudimentary call graphing technology, Code Property Graph offers a singular representation of multiple constructs stitched into one whole.
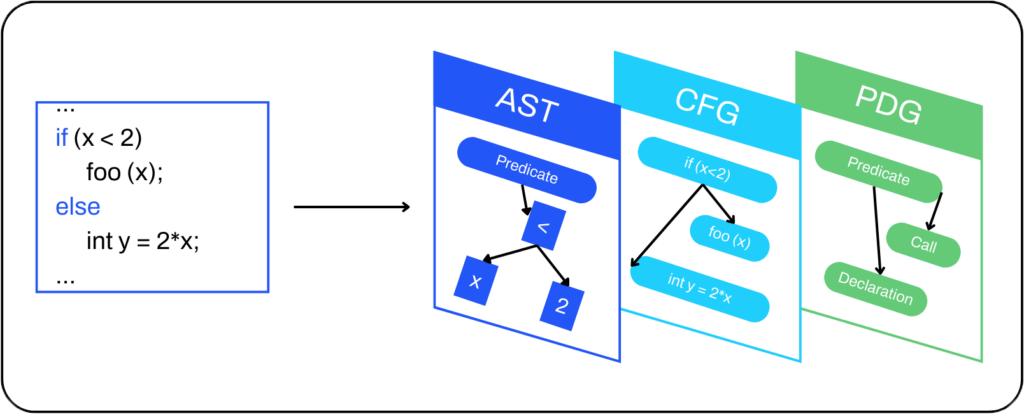
As a graph of graphs, Code Property Graph not only determines the simple call graph relationships between parts of code, but it also combines it with the power of control and data flow analysis to avoid the most common false-negative scenarios.
Reachability analysis in action — as Code Property Graph sees it
Let us take an example of a simple program call sequence for an application.
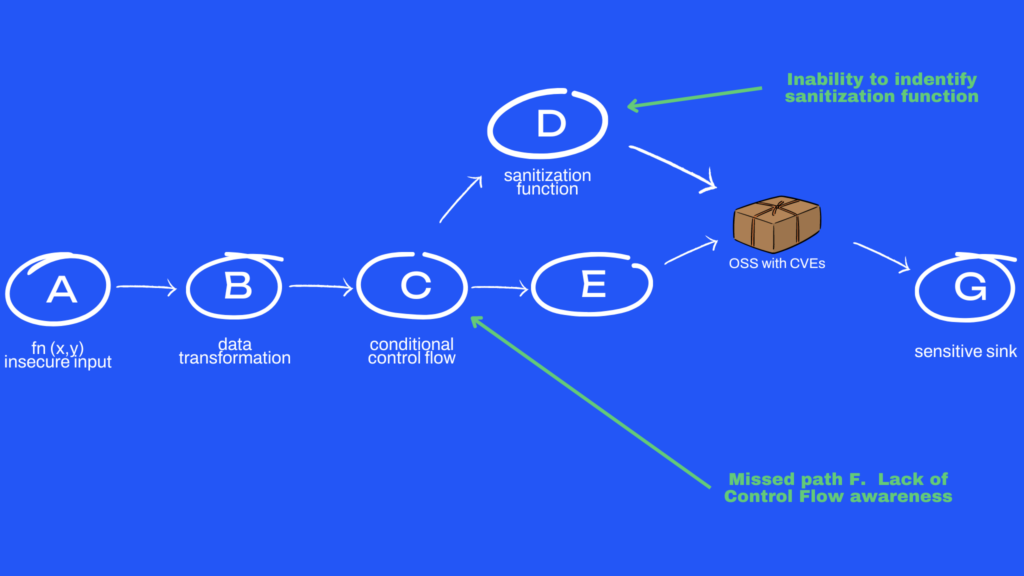 Sample call sequence
Sample call sequence
In the above example, we have a call sequence from an unsecured public input A. It further goes from A → B, does a data transform at B, branches at C with the conditional flow (C →D, C →E, C →F), with C → F being a package control condition. D’s and E’s path passes through OSS with CVE/s and from F through OSS without CVE, and all paths ending at G.
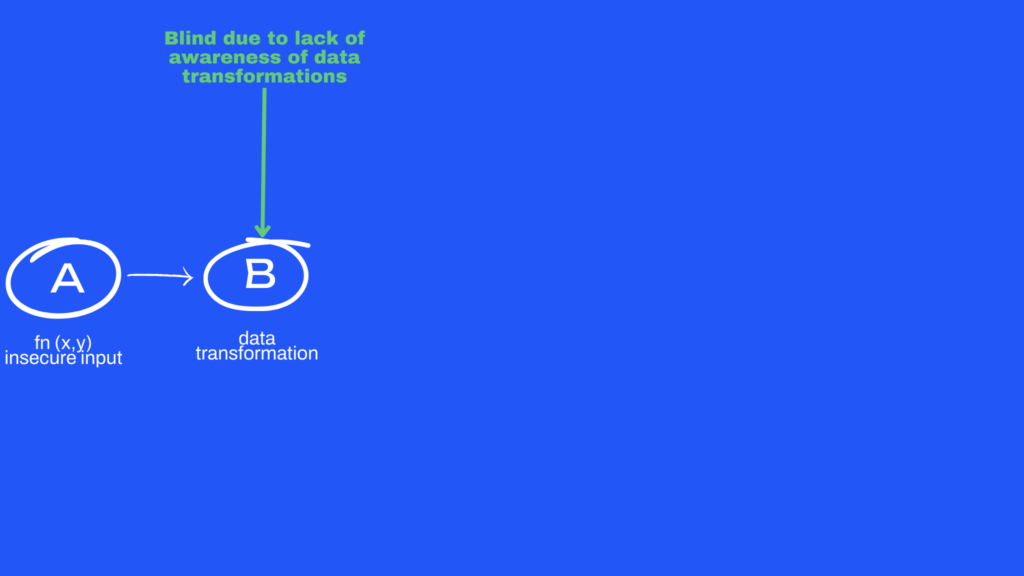 Basic call graph
Basic call graph
For a basic call graph analysis (which is used by several open-source vulnerability vendors), visibility for this call sequence will be limited (A →B) on account of their blindness to data transformations happening in step 2, which is a likely under-estimation of where a attacker’s reachable path was discarded.
For comparison, let us see a case with data transformation visibility, but without control flow awareness.
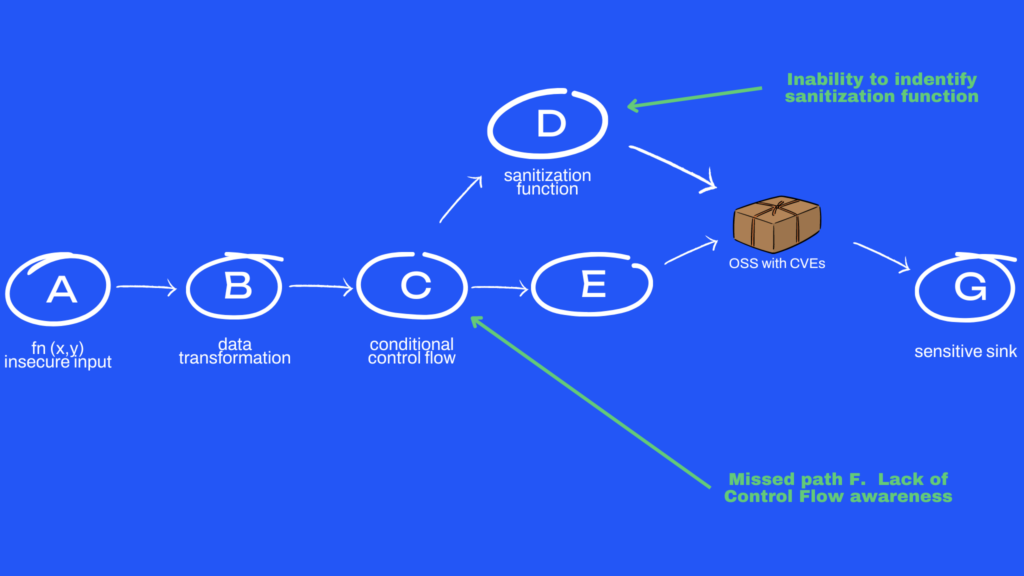 Call graph with data transformation visibility but without control flow awareness
Call graph with data transformation visibility but without control flow awareness
In the case above, we have a taint-aware call graph (basic data flow visibility), so it is able to trace out all of the potential paths from A to open-source packages. Unfortunately, because visibility is limited, it is not aware that a condition at C provides F as a safe call path to reach G. Neither is it aware of a sanitization function at D making a path through D non-viable for an attacker. The result makes both errors — both an overestimation and under-estimation of attacker reachable paths.
Finally, let’s see how Code Property Graph visualizes the situation.
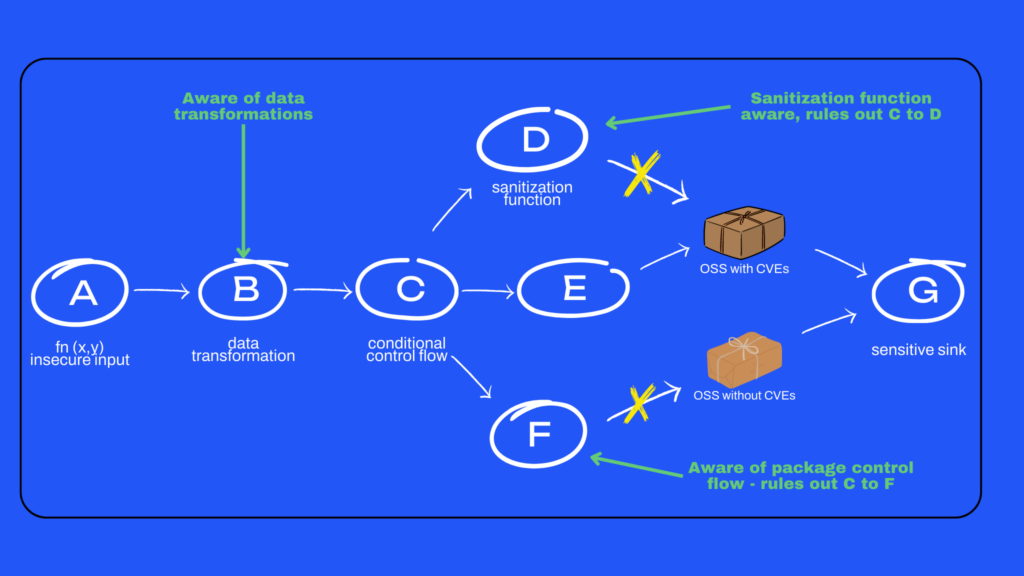 How does Qwiet AI visualize all of this?
How does Qwiet AI visualize all of this?
With Code Property Graph and its full power on display, we have no problem figuring out the entire code path sequence, thanks to the fact that path C → D and C → F are non-viable on account of data sanitization route and safe package control flow conditions.
Code Property Graph has higher fidelity in identifying “attacker reachable” paths as A → B →C→E, because it avoids both overestimating and under-estimating “attacker reachable” paths.
Evaluating Qwiet AI’s perZero platform with real-world applications
As discussed earlier in the blog, we subjected 49 customer/users’ apps using a commercial SCA solution, and we identified 2,761 potential OSS vulnerability tickets across 718 vulnerable packages. As a follow-up step, we subjected these same apps now through Qwiet AI’s intelligent software composition analysis. Here is what we found.
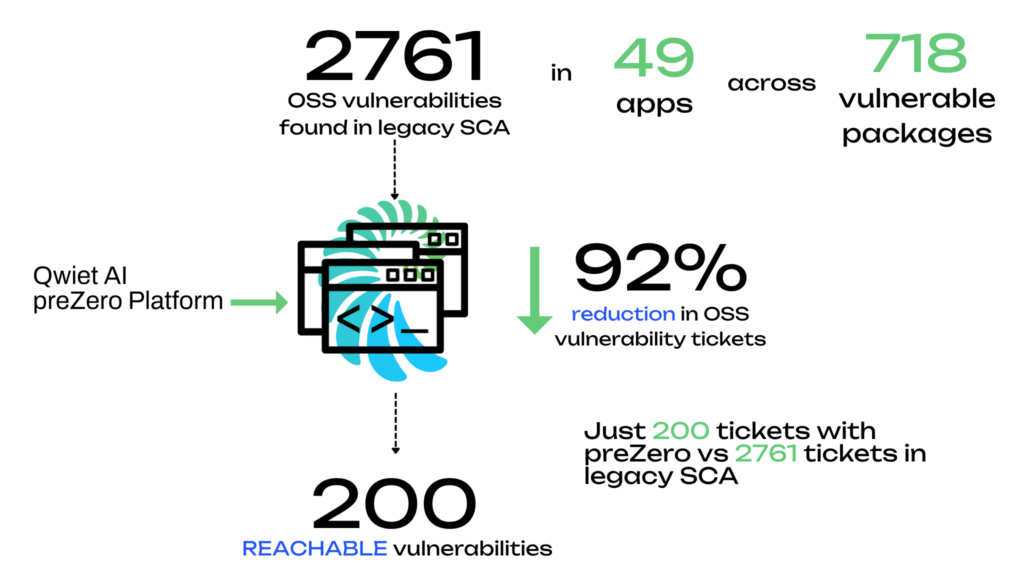
By focusing on only the reachable vulnerabilities, this particular customer had a dramatic 92% reduction in required fixes, (which can translate into a huge time and cost savings) but 200 fixes can still be a lot for an organization to tackle without incurring additional tech debt. That’s where exploitability comes into play.
Exploitability: Reachability’s new best friend
Reachability is a great way to prioritize, but you can further refine your results by utilizing Qwiet AI’s Blacklight feature. With Blacklight, we compare scan results against an up to date security threat feed to provide insight into which vulnerabilities have active exploits out in the wild. Clicking on the “Exploitable” filter in your results will show you all the vulnerabilities that will be attacked if not fixed before releasing your code. Combining Reachable and Exploitable findings can really help pinpoint the most important vulnerabilities and help you reduce the overall risk and number of fixes needed. Check out this post for more information on Blacklight.
TL/DR: Why should you trust Qwiet AI for prioritizing open-source vulnerabilities?
Qwiet AI offers the most intelligent solution on the market for solving open-source vulnerabilities issues. Of foremost importance is the Qwiet AI’s patented Code Property Graph approach to scanning, enhanced by our purpose built AI engine to uncover critical paths, eliminate long lists of vulnerabilities and reduce the time spent chasing bugs by more than 90 percent. Our solution has been featured in Dark Reading and has won raves from end-users in Gartner’s Peer Insights. And in tests against the OWASP Benchmark, it has achieved a true-positive rate of 100% and a false-positive rate of 25%—making it the best-in-class Static Application Security Testing (SAST) tool in terms of benchmark score.
Don’t just take our word for it, try out Qwiet AI’s perZero platform for yourself or reach out to us to schedule a demo!
