The Log4j Vulnerability: Still a Thing! Why...
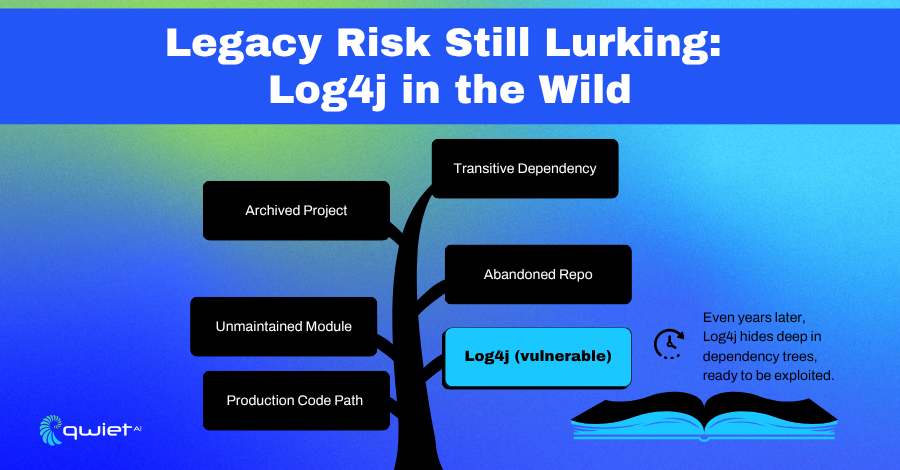
Key Takeaways Log4j is still present in many applications due to transitive dependencies and outdated libraries, making it a current, not just historical, threat. Traditional security tools often bury real threats like Log4j under layers of unrelated alerts, making it hard for developers to know what matters. Qwiet helps developers prioritize and fix real vulnerabilities […]